前言
NSS上看到了这个复习赛,13个取证题,统一附件,还是很有意思的,就打了下,也ak成功了,写下wp。
What the password?
描述:you got a sample of rick’s PC’s memory. can you get his user password?
获得PC机的密码,直接kit一把梭: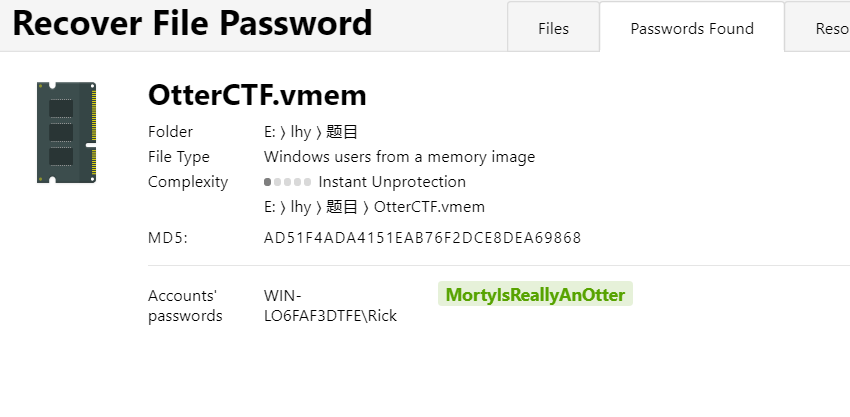
General Info
描述:Let’s start easy - whats the PC’s name and IP address?
获得PC机的名称和IP地址,netscan查看网络连接直接获取IP: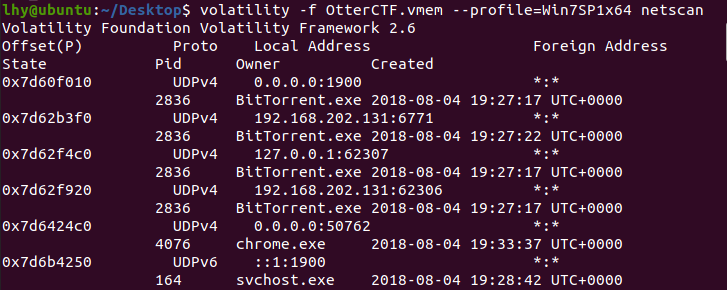
192.168.202.131
然后翻注册表: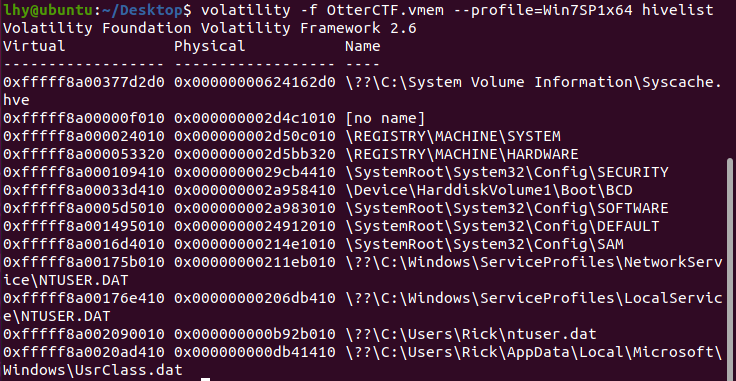
找SYSTEM: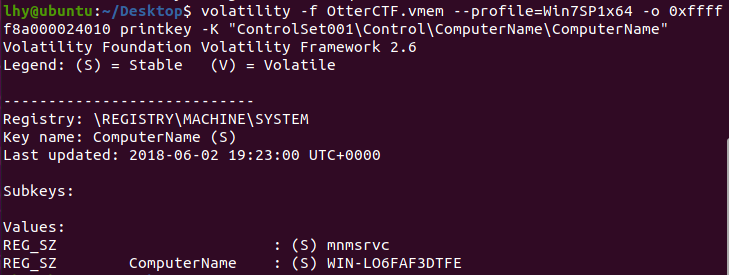
找到PC机名称:WIN-LO6FAF3DTFE
Play Time
描述:Rick just loves to play some good old videogames. can you tell which game is he playing? whats the IP address of the server?
找到Rick玩的游戏名称和其IP地址。直接netscan找一遍,发现LunarMS这个游戏,并且也有对应的IP: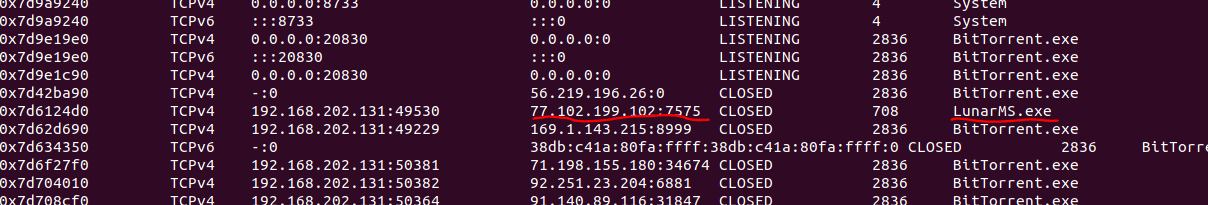
IP:77.102.199.107
Name Game
描述:We know that the account was logged in to a channel called Lunar-3. what is the account name?
找到Lunar-3这个服上的用户名,直接010搜索就可以找到了: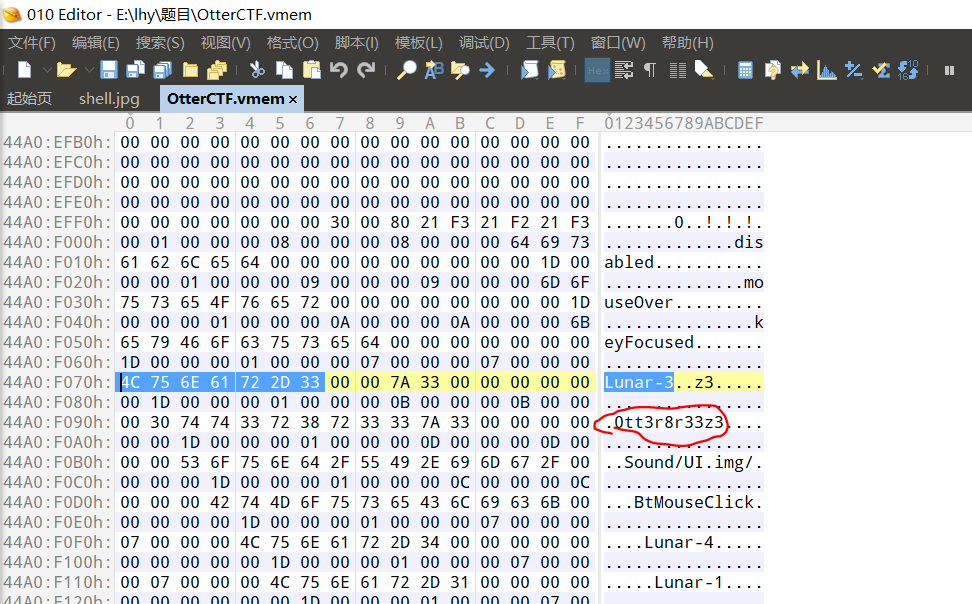
用户名:Ott3r8r33z3
Name Game 2
描述:From a little research we found that the username of the logged on character is always after this signature: 0x64 0x??{6-8} 0x40 0x06 0x??{18} 0x5a 0x0c 0x00{2} What’s rick’s character’s name?
用pslist找到游戏进程,然后dump下来,010按照那个十六进制字符串去找对应的部分,就可以找到了: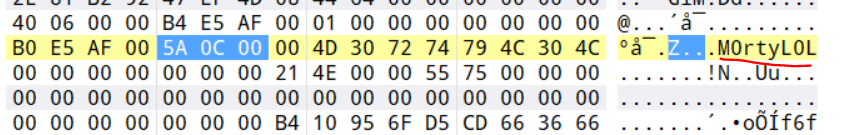
角色名:M0rtyL0L
Silly Rick
描述:Silly rick always forgets his email’s password, so he uses a Stored Password Services online to store his password. He always copy and paste the password so he will not get it wrong. whats rick’s email password?
根据描述可以了解到,密码在剪贴板里,用clipboard查看剪贴板就行了: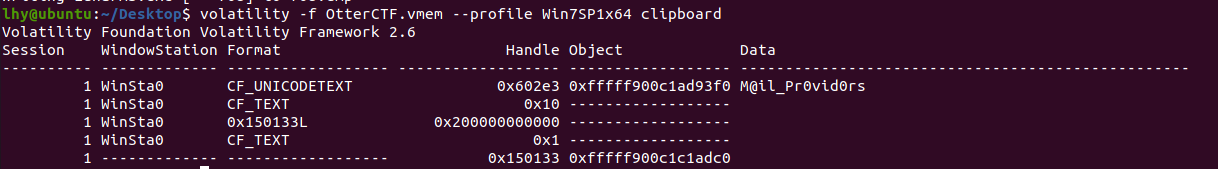
密码:M@il_Pr0vid0rs
Hide And Seek
The reason that we took rick’s PC memory dump is because there was a malware infection. Please find the malware process name (including the extension)
PC机中有一个恶意文件,我们要取得这个进程的名字。先去翻进程: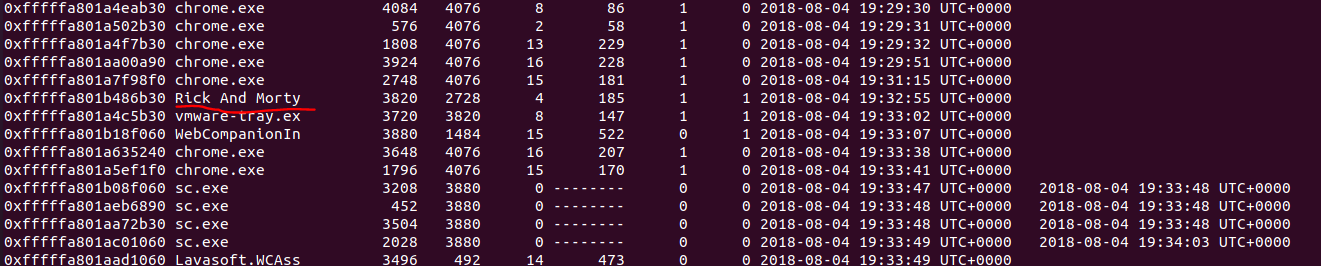
好像有个玩意不太一样,那就看看进程树: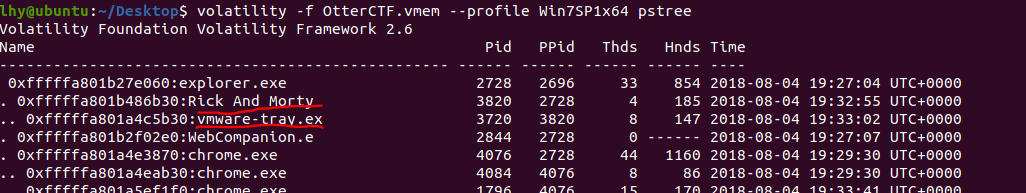
小黑子,露出鸡脚了吧,这下找到你咯。
程序名:vmware-tray.exe
Path To Glory
描述:How did the malware got to rick’s PC? It must be one of rick old illegal habits…
问我们恶意程序是怎样得到PC机的,怕不是Rick整了些什么好康的东西,直接先进行一波文件的找: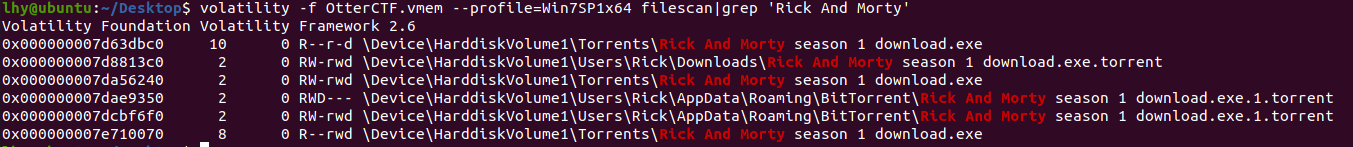
有三个种子文件,dump下来看,在其中一个中发现了问题: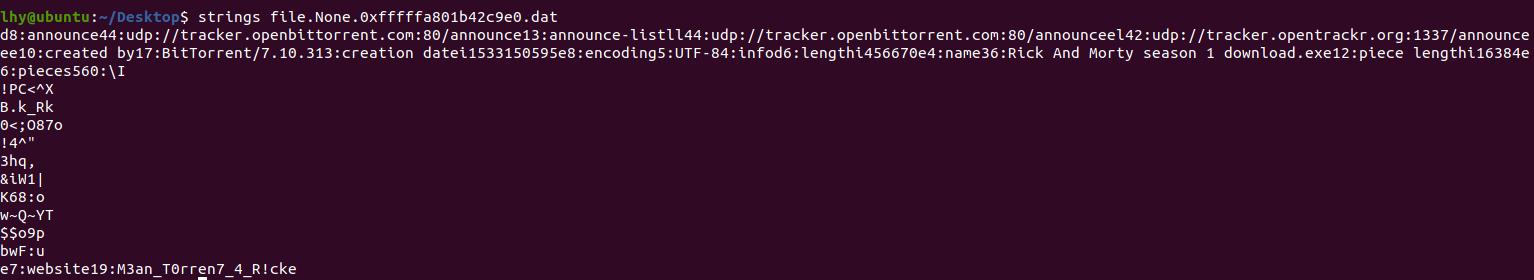
flag:M3an_T0rren7_4_R!ck,因为website字段的内容长度为19,所以那个e就不要进来。
Path To Glory 2
描述:Continue the search after the way that malware got in.
进一步探查恶意文件的来源,iehistroy里没东西,那就去找chrome浏览器进程:
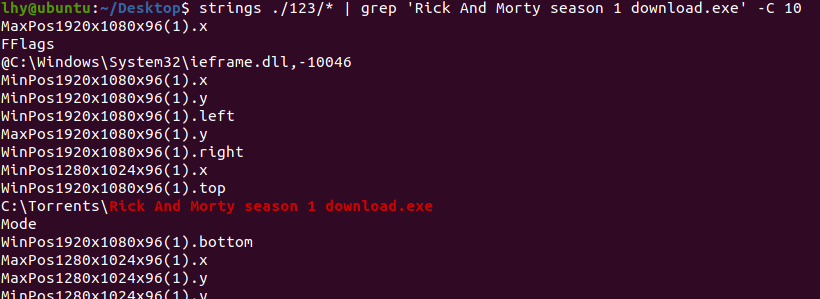
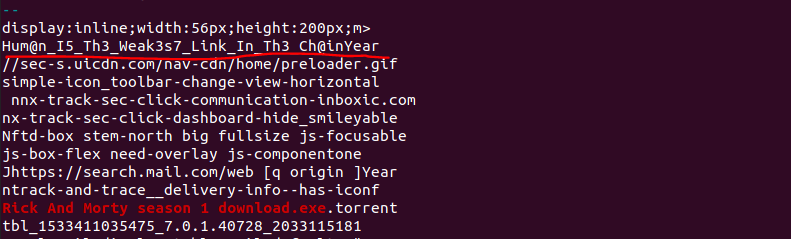
flag:Hum@n_I5_Th3_Weak3s7_Link_In_Th3_Ch@in
Bit 4 Bit
描述:We’ve found out that the malware is a ransomware. Find the attacker’s bitcoin address.
这个恶意进程是一个勒索软件,要我们找出攻击者的比特币账户地址。首先把恶意程序dump下来,然后拖入IDA中分析。也是很给面子,直接就给出来了: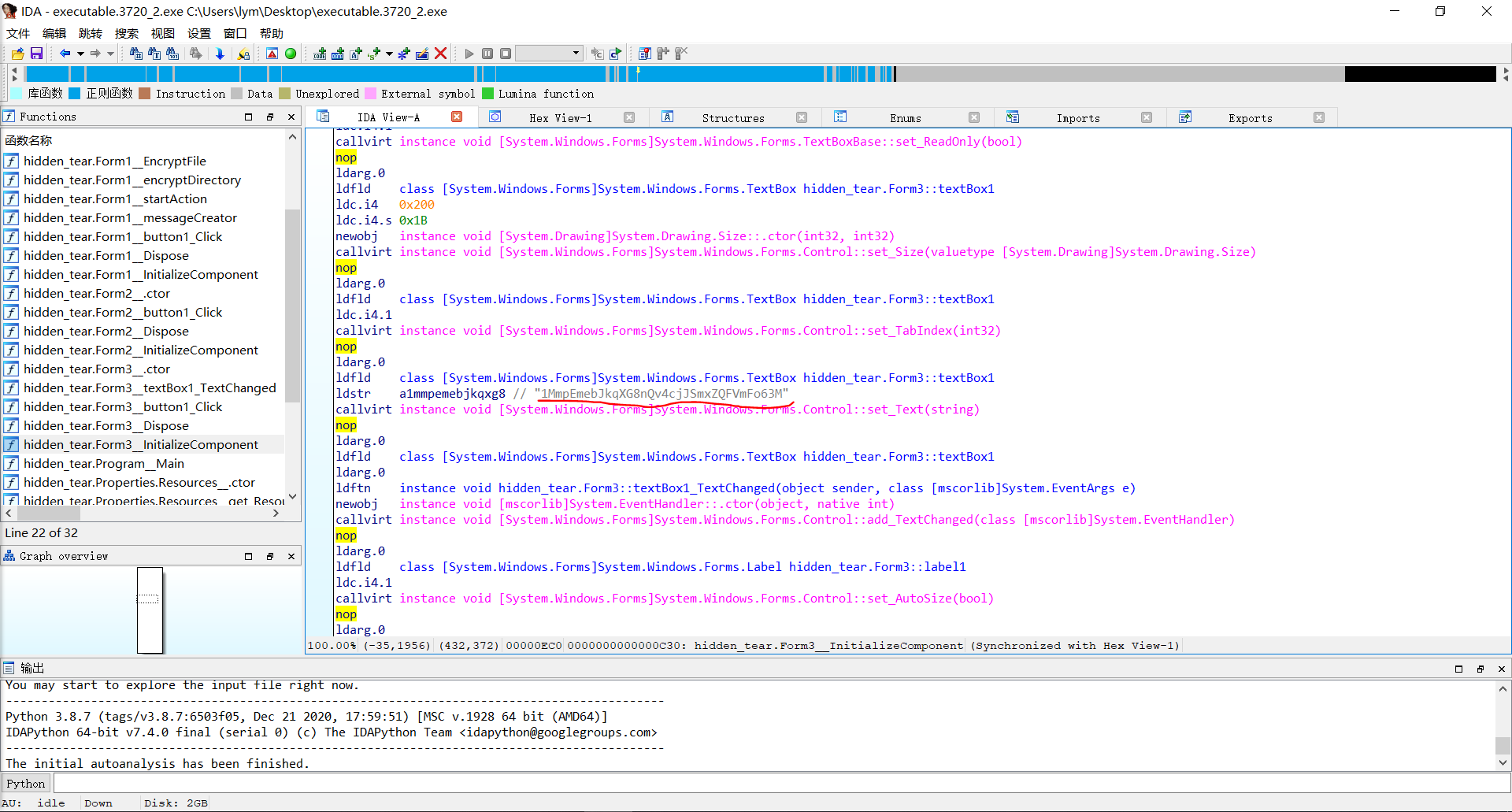
账户地址:1MmpEmebJkqXG8nQv4cjJSmxZQFVmFo63M
Graphic’s For The Weak
描述:There’s something fishy in the malware’s graphics.
这个程序里藏了东西,foremost提取:
发现有一张图,那个图片上就有flag:
Recovery
描述:Rick got to have his files recovered! What is the random password used to encrypt the files?
要获得恢复文件的密钥,我们先看IDA里的加密: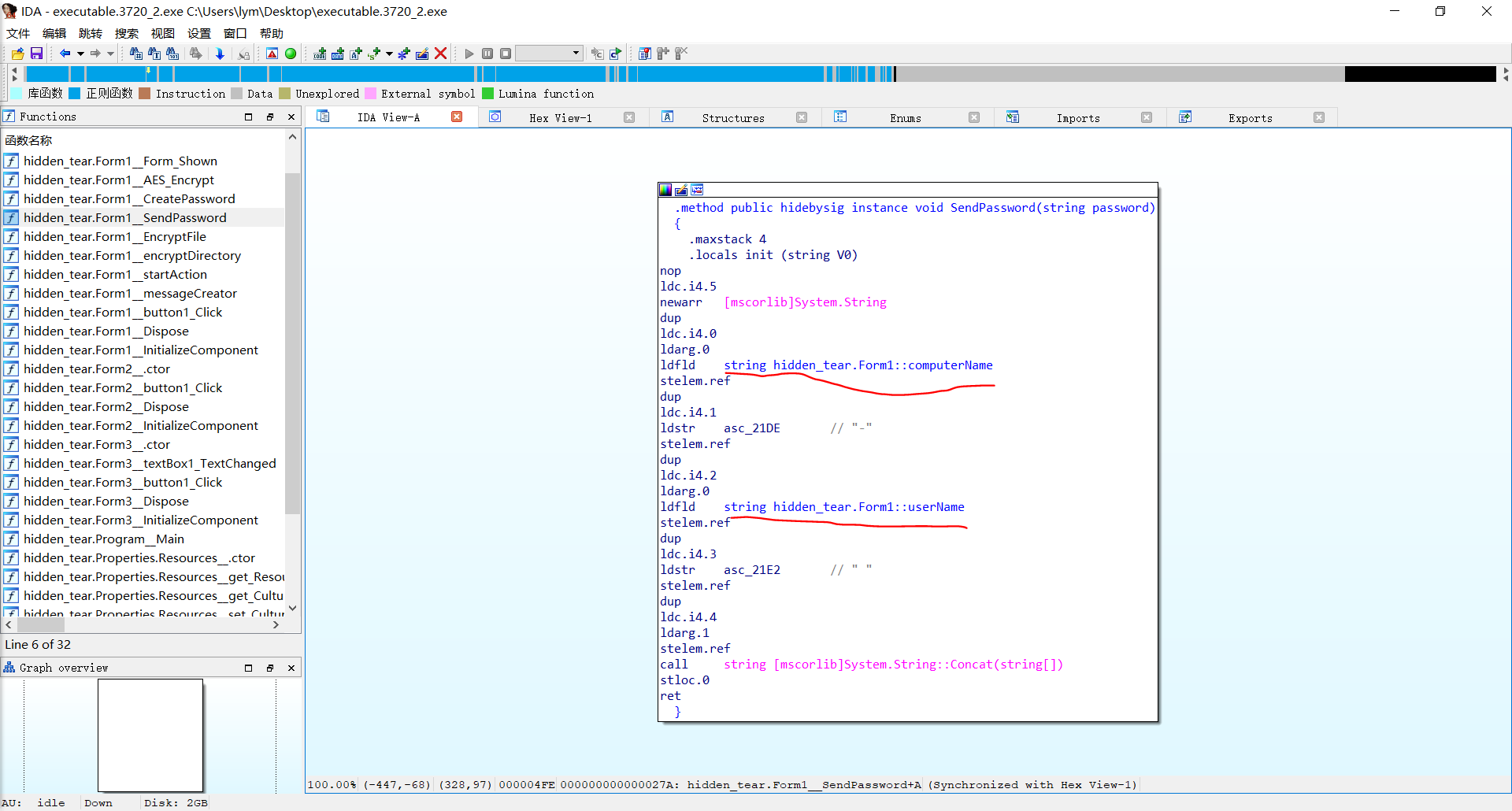
根据这个逻辑,发送密码,是把computerName和userName还有password拼接以后进行发送,那么我们直接在内存中搜索就可以了: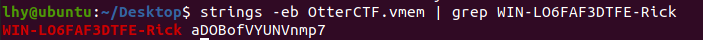
密码:aDOBofVYUNVnmp7
Closure
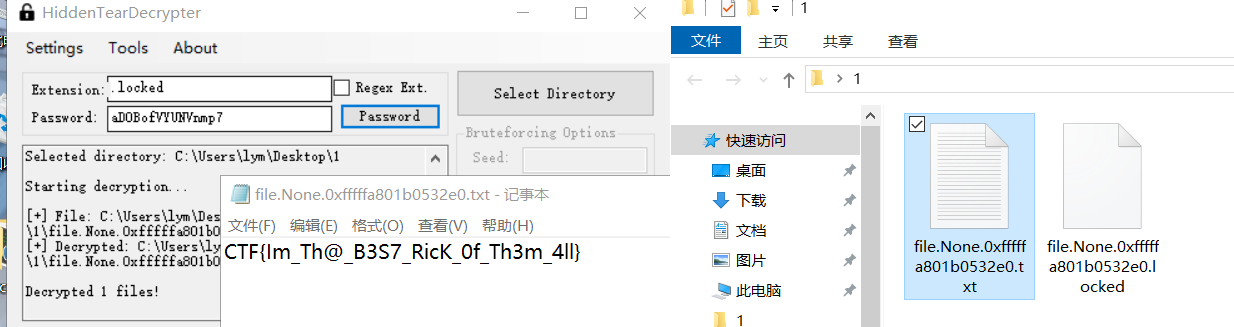
描述:Now that you extracted the password from the memory, could you decrypt rick’s files?
恢复文件,之前在内存中发现有一个flag.txt,dump下来之后使用HiddenTearDecrypter工具进行解密即可获得最后的flag: